
New opportunities for hackers: Increasing number of less sophisticated attacks on OT systems. Mandiant has been monitoring groups of hackers who claim to broker or sell access to Internet-enabled OT systems since at least 2012, but the incidence and relative severity of the incidents have increased significantly in recent years. An analysis.
Attacks on control processes in operational technology (OT) are considered to be very complex, because the targeted disruption or modification of a control process for a specific purpose is usually not only very complicated, but also time-consuming and resource-consuming.
More attacks - but also unpolished
However, Mandiant Threat Intelligence has also observed simpler attacks, in which groups of hackers with different technical skills and resources used common IT tools and methods to gain access to and interact with OT systems.
These activities are usually not very technically sophisticated and are also not geared towards specific companies. The attackers pursue ideological, self-centered or financial goals and then use the possibilities offered by the numerous OT systems connected to the Internet. Since the hackers are not aiming for specific results, they simply attack any target accessible via the Internet.
Cyber Physical Intelligence team
The Cyber Physical Intelligence team at Mandiant has observed an increasing number of attacks on Internet-enabled OT systems in recent years. In this blog post we present some previously unpublished attacks and show the connections to publicly known security incidents. These attacks do not seem to have had a significant impact in the real world, but since they are becoming more common and could be serious, we provide an analysis and provide information about the potential risks and consequences.
Attacks on Internet-enabled OT systems are increasing
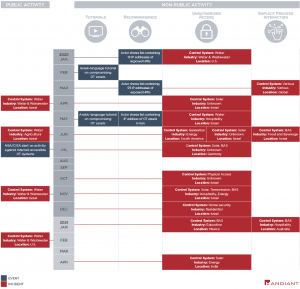
Some of the less sophisticated OT attacks observed; Jan. 2020 to April 2021 (Photo: Fireeye / Mandiant)
Mandiant has been monitoring groups of hackers who claim to broker or sell access to Internet-enabled OT systems since at least 2012, but the incidence and relative severity of the incidents have increased significantly in recent years. In most cases, the attackers try to monetize access to the compromised systems, but some also simply pass their knowledge on. Recently, we have seen mostly less experienced attackers who use familiar tactics, techniques, and processes (TTP) and standard tools to gain access to, interact with, or retrieve data from Internet-connected resources. There have rarely been such attacks in the past.
These rather less sophisticated attacks had different targets in various industries - from solar modules and water control systems to building automation (BA) and security systems in academic institutions and private households. Some targets in critical infrastructures are very sensitive, while others pose almost no risk.
Timeline shows significant growth
In the timeline below, you can see some publicly known and previously unpublished attacks on OT systems that Mandiant observed between 2020 and early 2021. We would like to point out that it is entirely possible that an interaction with the processes took place in these incidents. However, this cannot be reliably proven, as the evidence usually comes from the attackers themselves. A blog post on Fireeye or Mandiant shows an extended analysis and individual steps.
More at FireEye.com
About Trellix Trellix is a global company redefining the future of cybersecurity. The company's open and native Extended Detection and Response (XDR) platform helps organizations facing today's most advanced threats gain confidence that their operations are protected and resilient. Trellix security experts, along with an extensive partner ecosystem, accelerate technology innovation through machine learning and automation to support over 40.000 business and government customers.
