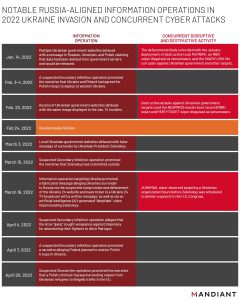
Research by Mandiant provides a comprehensive analysis of the various disinformation campaigns that have been observed since the Russian invasion of Ukraine began. New insights into those responsible for the attacks point to hacking groups supported by the Russian, Chinese and Iranian governments.
The report reveals new disinformation campaigns that have not previously been reported, makes new attributions to Chinese and Iranian hacker groups that have simultaneously launched their own disinformation campaigns, and illustrates that the various cyber attacks have been accompanied by disruptive and destructive military attacks on Ukraine.
Disinformation campaigns against Ukraine
One of the report's senior authors, Senior Analyst Alden Wahlstrom, summarizes the research as follows:
“Some of these activities are well known and have been reported. However, this new report highlights how well-known actors and campaigns can be used or refocused to pursue emerging security interests – including large-scale conflict. For years, analysts have documented that Ukraine is of major strategic interest to Russia and a testing ground for Russian cyberattacks that are then deployed elsewhere. Now we see pro-Russian actors using the tools and campaign infrastructure developed over time (in whole or in part) to target Ukraine.”
Key findings from Mandiant's research
- Dubbed the “Secondary Infection,” the Russian influence campaign began before the invasion and continued to spread misinformation about President Volodymyr Zelenskyy thereafter.
- A new ghostwriting operation, which Mandiant is publicly attributing to the group for the first time, used compromised documents to publish fake content. The aim: to spread the claim that a Polish criminal ring is taking organs from Ukrainian refugees for illegal trafficking in the European Union.
- A pro-Iranian campaign previously unnamed by Mandiant is now being labeled "Roaming Mayfly" as it may be linked to Iran's "Endless Mayfly" influence campaign. Citizen Lab reported on this in 2019.
- The pro-Chinese DRAGONBRIDGE campaign has changed its communication: it now produces content in English and Chinese, echoing the portrayals circulated by the Russian state media and influence campaigns.