Ultra high-speed attacks on ESXi servers and VMware virtual machines. Sophos researchers discover new Python ransomware. The report entitled “Python Ransomware Script Targets ESXi Server for Encryption” provides a deeper insight.
Sophos has released details of a new Python-based ransomware cybercriminals are using to attack and encrypt virtual machines running on ESXi hypervisors. In the report entitled “Python Ransomware Script Targets ESXi Server for Encryption”, the experts at Sophos Labs describe a high-speed attack that took less than three hours from intrusion to encryption.
Targeting VMware's ESXi platforms
"This is one of the fastest ransomware attacks Sophos has ever investigated, and it appears to be targeting the ESXi platform," said Andrew Brandt, principal researcher at Sophos. “Python is a programming language not commonly used for ransomware. However, Python is pre-installed on Linux-based systems such as ESXi, so Python-based attacks on such systems are possible. VMware's ESXi servers are an attractive target for ransomware criminals due to their ability to simultaneously attack multiple virtual machines running potentially mission-critical applications or services. Attacks on hypervisors can be both rapid and extremely devastating. Ransomware groups like DarkSide and REvil target ESXi servers in their attacks.”
Course of the attack under investigation
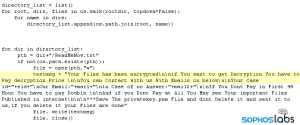
The investigation revealed that the attack began at 0:30 a.m. on a Sunday when a TeamViewer account was hijacked that was running on a computer that also had access data for the domain administrator.
Just 10 minutes later, the attackers used the Advanced IP Scanner tool to search for targets on the network. SophosLabs believe that the ESXi server was vulnerable on the network because it had an Active Shell, a programming interface that IT teams use for commands and updates. This enabled the cybercriminals to install a secure network communication tool called Bitvise on the domain administrator's machine, which gave them remote access to the ESXi system, including the storage used by the virtual machines. At around 3:40 a.m., the ransomware was activated and the ESXi servers encrypted hard drives.
Note for more security
“Administrators running ESXi or other hypervisors on their networks should follow security best practices. This includes using strong passwords and using multi-factor authentication wherever possible,” says Brandt. “The ESXi Shell can and should be disabled whenever staff are not using it for routine maintenance, such as during patch installation. The IT team can control this using either the server console controls or the software management tools provided by the vendor.”
Endpoint products, such as Sophos Intercept X, protect systems by detecting the actions and behaviors of ransomware and other attacks. Attempts to encrypt files are blocked accordingly. Specific safety notices for ESXi hypervisors are available online here.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.