
USB mass storage devices provide a quick, easy way to move and share data when digital transmission is not possible. However, the high risk of theft and loss makes USB mass storage devices a security nightmare for corporate security.
The current widespread remote work has exacerbated these problems. The volume of data downloaded to USB mass storage devices by employees is according to the DG Data Trends Report has increased by 19 percent since the beginning of the COVID-123 crisis. This suggests that many employees are using these devices to take large amounts of data home with them. As a result, hundreds of terabytes of potentially sensitive, unencrypted data are outside of corporate security, significantly increasing the risk of data loss. However, effective implementation of USB control and encryption can greatly improve protection against the inherent dangers of these devices.
Basics: USB control and encryption
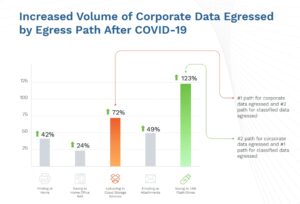
The report shows that the use of USB sticks with important company data has risen sharply (Source: DG Data Trends Report by Digital Guardian)
USB control and encryption refers to a number of techniques and practices used to secure device access to USB ports. These form an important part of endpoint security and help protect sensitive databases from loss and computer systems from threats that can be deployed via physical plug-in USB devices, such as malware.
There are several ways to implement USB control and encryption. The most restrictive approach is to block the use of USB devices altogether, either by physically covering the USB ports on the endpoints or by disabling USB adapters throughout the operating system. However, for the vast majority of businesses, given the large number of peripherals that rely on USB ports, this is not a viable approach.
Alternatively, less draconian physical measures can be combined with the use of encryption to protect sensitive data, even if a flash drive containing data is lost or stolen. The simplest, but usually also the most expensive, way is to buy devices that already have robust encryption algorithms built into them. A cheaper option is to implement and enforce specific IT guidelines for the use of USB devices. These can either be policies that only allow employees to use certain approved USB devices whose file systems have been manually encrypted, or that require certain files to be encrypted before they can be transferred to a USB storage device.
Tunable controls for nuanced security
The standard controls for USB ports that are offered as part of most operating systems are usually quite limited in their functionality. Security teams have the choice of leaving them completely open, marking them as read-only, or disabling them entirely. For a more nuanced approach, however, a higher level of granular control can be achieved using security applications.
For example, it can be specified that every inserted USB device must tell the operating system exactly what type of device it is as part of the connection protocol. Using USB control applications, administrators can use this information to restrict or block certain types of USB devices on certain endpoint ports. For example, the use of USB mice can be permitted via the port, but storage devices such as USB sticks can be prohibited.
Some security solutions go even further and make it possible to set up rules that regulate USB ports down to an individual level. This includes specifying exactly what types of files can be copied or transferred over a particular USB port, or specifying that a particular port can only be used by devices from a pre-approved whitelist (based on their serial number). Such controls can be extremely effective in preventing improper data transfers or malicious actions such as attempting to upload malware using an unauthorized USB stick.
Centrally controlled solution saves considerable logistical effort
A corporate network can contain hundreds or even thousands of end devices with one or more USB ports. As a result, control and encryption solutions that cannot be managed individually but rather centrally are much easier to implement and manage. This is especially true at the present time when remote maintenance protocols make it nearly impossible to effectively manage devices in any other way.
While USB portable drives are seen by employees as a fast, convenient way to move or store data, they pose a security risk for businesses. However, implementing USB control and encryption solutions provide security teams with the tools they need to deal with threats using USB devices for corporate networks and sensitive corporate data.
[starboxid=6]
