
m-privacy develops remote-controlled web browsers for maximum internet security in industry, healthcare and government. ProSoft presents safe surfing with TightGate-Pro, whereby the screen display of the browser is delivered as a video data stream.
The use of the internet is an integral part of working life. However, safe surfing is now only possible to a limited extent, as cyber criminals specifically use the web browser to smuggle dangerous malware onto workstation computers. Under the slogan "Distance creates security", ProSoft is now presenting TightGate-Pro from m-privacy GmbH for secure surfing, which offers a new form of Internet security: With TightGate-Pro, the browser is run on highly hardened servers outside the internal network . The workstation computer only receives the screen display of the browser as a video data stream via a function-specific protocol.
Surfing with full isolation of the internal network
"TightGate-Pro enables the fully functional use of the Internet while at the same time isolating the internal network from the associated dangers," reports Robert Korherr, Managing Director of ProSoft GmbH. TightGate-Pro from m-privacy GmbH is a remote-controlled browser system (ReCoBS), literally translated as "remote-controlled web browser". This physically separates the execution environment of the web browser from the workstation computer. The system thus shields the internal network from the Internet and reliably and preventively prevents attacks that exploit security gaps in Internet browsers.
Remote-controlled screen output as video data stream
This means that the web browser is no longer running on the workstation. Instead, the dedicated TightGate server set up in the DMZ (demilitarized zone) takes over the execution of the browser. The workstation computer only receives the screen output from the browser as a video data stream via a function-specific protocol. The screen output and the sound output are displayed on the monitor or loudspeaker of the workstation computer. At the same time, the virtual browser can be remotely controlled from the workstation using the mouse and keyboard. With regard to the “look and feel”, there is practically no difference to the local browser. A packet filter between TightGate-Pro and the computer workstations ensures that only the image data stream from TightGate-Pro can actually reach the clients, but not other network accesses.
Physical separation creates preventive security
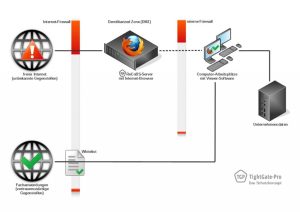
The TightGate Pro principle: the user only receives a live video of his remote browser usage (Image: m-privacy).
Because of this physical separation, even calling up a compromised website has no consequences for the internal network. “This makes TightGate-Pro far superior to any other solution based on local virtualization or sandbox in terms of security. Only the physical separation of the web browser's execution environment creates the preventive security that modern infrastructures require in view of the increasing attack pressure on the Internet, ”said the managing director.
Client programs for control and file exchange
TightGate-Pro consists of the dedicated ReCoBS server and the client programs TightGate-Viewer, TightGate-Schleuse and MagicURL (link switch). The TightGate Pro server represents the execution environment for the browser, while the client programs are responsible for display, control and file exchange. It is important that the viewer corresponds to the state of the art and does not leave any attack vectors open. Instead of powerful transmission protocols such as RDP, ICA, HDX or the local X server, TightGate-Pro uses a function-specific protocol so that no malicious code can be transmitted to the client.
TightGate-Pro is BSI-certified according to Common Criteria EAL3 + and GDPR-compliant. The tool has been used successfully in government agencies, financial institutions, industrial companies and critical infrastructures for 15 years.
More at ProSoft.de
About ProSoft ProSoft was founded in 1989 as a provider of complex software solutions in the large computer environment. Since 1994 the company has focused on network management and IT security solutions for modern, heterogeneous Microsoft Windows infrastructures, including Mac OS, Linux as well as mobile environments and end devices. The experts manage efficient software and hardware for corporations and medium-sized companies and have established themselves as specialists for IT security. In addition, as a value-added distributor (VAD), ProSoft supports manufacturers with the “go-to-market” and the launch of new solutions in the German-speaking part of Europe.
