The move to serverless computing is picking up speed. According to a 2019 survey, 21% of companies have already adopted serverless technology, while 39% are considering it. Trend Micro provides the corresponding whitepaper for download.
Serverless technology is attractive to many companies because it allows them to focus on building better code for their applications rather than managing and securing the infrastructure required to run the applications. Trend Micro's research whitepaper "Securing Weak Points in Serverless Architectures: Risks and Recommendations" provides security considerations for serverless environments and helps users make their serverless environments as secure as possible. The focus is on the services offered by AWS, which has the broadest range of offers in this market.
Serverless computing is a technology that supports backend services so that companies can delegate certain responsibilities, including capacity management, patching, and availability, to cloud service providers (CSPs) such as Amazon Web Services (AWS). With serverless computing, backend applications can be created without being directly involved in availability and scalability. The term “serverless” does not mean, however, that this computing model does not use any servers at all, but that companies no longer have to be directly involved in the maintenance and protection of servers.
Serverless technology more secure than other cloud computing models
The security of the infrastructural computing components of these architectures is largely guaranteed by the CSPs (Cloud Service Providers). Because of this, serverless technology is considered to be relatively more secure than other cloud computing models. But like any other technology in existence, it is not immune to risks and threats.
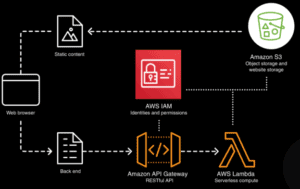
Networked services in a serverless architecture
To understand how a serverless architecture works, you need to know which different services are involved. This post is about an AWS serverless architecture.
Amazon S3
Amazon Simple Storage Service (Amazon S3) is an object storage service for scalable amounts of data that supports a variety of use cases, such as mobile applications, big data analytics and IoT devices. Amazon S3 makes it possible to manage objects, which are then stored in buckets via APIs.
AWS Lambda
One of the most popular serverless services is AWS Lambda. It enables businesses to run code without the hassle of deploying and maintaining servers. Developers only pay for the number of instances when the code is triggered. With AWS Lambda, you don't have to manage hardware or make sure the operating system and all installed applications are up to date.
Amazon API Gateway
Amazon API Gateway allows you to easily and efficiently create, publish, maintain, monitor and secure APIs. The service acts as a portal for applications that can access backend service functions or data via RESTful APIs and WebSocket APIs.
AWS IAM
Using AWS Identity and Access Management (AWS IAM), developers can manage security information and permissions to confirm access to serverless services and resources.
Misconfigurations and unsafe coding practices
Larger CSPs such as AWS apply the Least Privilege Policy when assigning permissions for certain tasks. They also take the standard denial approach, which ensures that any service can only communicate or be accessible to another service if the necessary permissions are granted. The manual assignment and verification of privileges ensures greater security. However, this can be difficult for users, especially given a complex mix of interconnected services. As a result, they could introduce or overlook misconfigurations and risks such as the following in the security of serverless services.
Amazon S3
Amazon S3 buckets left open or freely accessible could be a door for malicious actors to look for sensitive data. Critical data or pieces of code that shouldn't be publicly visible could also be exposed if Amazon S3 buckets are used to host content for which they were not intended.
AWS Lambda
AWS Lambda functions could be exploited by malicious actors through injection techniques on faulty or vulnerable code. Sensitive data could also be exposed if the code of an AWS Lambda function is designed in such a way that it returns variables and is accessible to external services. Malicious actors could also exploit the credentials stored as variables in AWS Lambda functions to gain access to a user's account. In addition, malicious code could be used to store malicious tools and scripts in the / tmp folder of an AWS Lambda execution environment. Files here could be persistent enough to launch attacks or exfiltrate sensitive data.
Amazon API Gateway
As soon as an Amazon API gateway endpoint is open and unprotected, it could trigger a denial-of-service (DoS) attack in order to compromise or shut down the service behind it. Malicious actors intent on causing financial damage to a company can also misuse an open Amazon API Gateway endpoint to continuously poll an AWS Lambda function to drive the company's bills high.
AWS IAM
Perhaps because of time constraints, developers sometimes make the guidelines excessively permissive to ensure communication between system components. This is made easy with AWS IAM. But this relaxation of permissions naturally affects the security of the serverless services that AWS IAM is used with.
Bad code risks
To make the risks of implementing bad code on a serverless system even clearer, the researchers created a proof-of-concept that includes an AWS Lambda function with high permissions. The following video shows how bad coding practices allow malicious actors to successfully change the time-out of the AWS Lambda function and then perform other activities such as privilege escalation and data exfiltration.
Impact of Security Risks on Businesses
Serverless services include stateless functions, and therefore the data in these services remains in the cache and is not stored in memory. When moving data from serverless services to off-site locations, organizations need to be careful about how the data is moved to avoid data leakage. One such data leak happened when a database containing half a million sensitive legal and financial documents was exposed due to a misconfiguration when changing access policies.
It is also important to know where data is stored in order to avoid compliance problems, such as those known as over 36.000 prisoner records from various penal institutions in the USA because a data store connected to a cloud-based application was accessible . The compromise of a company's application or service could also disrupt business operations and damage its reputation.
Security for serverless services and installations
The shared responsibility model, in which both the CSP and the user assume responsibilities for the security of the cloud environment, also applies to serverless computing. The research project presents ways in which serverless services and installations can be protected against risks and threats using best practices and security solutions. The whitepaper "Securing Weak Points in Serverless Architectures: Risks and Recommendations" provides further details on the subject.
Directly to the whitepaper at Trendmicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.