
Team82 discovers 15 vulnerabilities in Siemens' network management system (SINEC NMS). Vulnerabilities allow denial of service attacks, credential harvesting, and remote code execution.
The security researchers from Team82, the research department of the specialist for the security of cyber-physical systems (CPS) in industry, healthcare facilities and companies Claroty, have discovered a total of 15 vulnerabilities in the Siemens network management system (SINEC NMS). For example, CVE-2021-33723 allows attackers to escalate their privileges and CVE-2021-33722 allows remote code execution using a path traversal attack. All versions prior to V1.0 SP2 Update 1 are affected. Siemens advises users to update to V1.0 SP2 Update 1 or a later version. In addition, Siemens has published corresponding safety instructions.
Vulnerabilities: Siemens provides update
Industry 4.0 is driven by strong networking to increase efficiency and enable 24/7 data exchange between different devices. In order to be able to provide such functionality, network management systems (NMS) monitor and maintain the industrial network elements. In addition, network data is leveraged by process functions via OPC UA and other industry protocols to enable correlation of process and network telemetry, ensuring process continuity and monitoring. SINEC NMS from Siemens is a popular tool for identifying control systems and processes in the network, their respective connections and dependencies, and their status. The diagnostics generated by the tool and the network topology allow operators to detect and respond to events, improve configurations, monitor device health, and make firmware upgrades and configuration changes.
“Living-Off-The-Land” attack possible
To do this, SINEC has access to the login information, cryptographic keys and other secrets. However, this can also allow cybercriminals to launch an effective "living-off-the-land" attack, where legitimate credentials and network tools are misused to perform malicious activities. If they have access to SINEC, they can use it to explore the network, move laterally and escalate their privileges. Team82 found 15 different vulnerabilities in SINEC that could allow an attacker to escalate their privileges, gain administrative rights to the system, steal confidential information, trigger a denial of service attack on the platform, and even remote code run on the host machine using NT AUTHORITY\SYSTEM privileges.
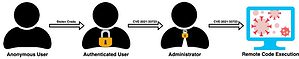
Attackers can combine the vulnerabilities at Siemens (SINEC NMS) to run code remotely (Image: Claroty)
Siemens has since made fixes available for several security vulnerabilities and advises all users to update to V1.0 SP2 Update 1 or a later version. Team82 would like to expressly thank Siemens for their cooperation in uncovering these vulnerabilities, for quickly confirming the results and for quickly resolving these security gaps.
How this attack looks in detail, a proof of concept and further information can be found in the corresponding blog post by Claroty.
More at Claroty.com
About Claroty Claroty, the Industrial Cybersecurity Company, helps its global customers discover, protect and manage their OT, IoT and IIoT assets. The company's comprehensive platform can be seamlessly integrated into customers' existing infrastructure and processes and offers a wide range of industrial cybersecurity controls for transparency, threat detection, risk and vulnerability management and secure remote access - with significantly reduced total cost of ownership.
