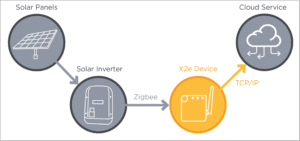
In late 2019, the Red Team at Mandiant, a FireEye unit, discovered a number of vulnerabilities in Digi International's ConnectPort X2e device.
Mandiant's research focused on the SolarCity (now Tesla) renamed X2e device, which is used to collect data in private solar systems. A typical setup provides that SolarCity provides a customer with a gateway (the X2e device) and this is connected to the Internet via an Ethernet cable in the customer's home network. In this way, the device can interpret and send measured energy values. Hackers have succeeded in gaining access to the device remotely.
Fixed vulnerability - further attacks threatened
In the meantime, Mandiant has fixed the weaknesses in cooperation with Digi International and Tesla. But according to Jake Valletta, Director, Mandiant, "Any device that is added to a home network that can be accessed remotely - be it a baby monitor or a VoIP device - is a security vulnerability." The Mandiant experts agree sure: we will see further attacks on such devices.
In two blog posts, FireEye sheds light on applied hardware attacks, including the methods and tools used by the hackers.
Part 1 provides an overview of the X2e device, an initial network-based exploration, PCB inspection techniques, physical debugging interface probing, chip-off techniques and firmware analysis. Using these methods, Mandiant was able to successfully compromise the X2e device remotely based on hard-coded credentials (CVE-2020-9306) even without administrative privileges.
Part 2 deals with how Mandiant used power glitching attacks to gain a privileged shell locally on the device. The CVE-2020-12878 vulnerability made it possible to remotely extend the privileges and give the hacker administrator rights. Taken together, these two vulnerabilities - CVE-2020-9306 and CVE-2020-12878 - result in a complete remote compromise of the X2e device.
Go to Part 1 at FireEye.com Go to Part 2 at FireEye.com
About Trellix Trellix is a global company redefining the future of cybersecurity. The company's open and native Extended Detection and Response (XDR) platform helps organizations facing today's most advanced threats gain confidence that their operations are protected and resilient. Trellix security experts, along with an extensive partner ecosystem, accelerate technology innovation through machine learning and automation to support over 40.000 business and government customers.