Customer access is required for full use of OpenAI's AI system ChatGPT. Russian hackers are currently looking for ways to bypass this access to use ChatGPT to achieve their malicious goals. But that's what a lot of hackers want right now. Conversation notes from the dark web.
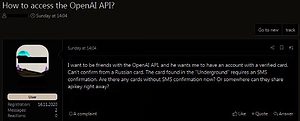
Check Point Research (CPR) is monitoring attempts by Russian hackers to bypass OpenAI restrictions to use ChatGPT for malicious purposes. In underground forums, hackers are discussing how to bypass controls of IP addresses, payment cards and phone numbers - all of which are necessary to access ChatGPT from Russia. CPR shares screenshots of what they saw and warns about the rapidly growing interest in ChatGPT by hackers of all countries to expand their criminal circles.
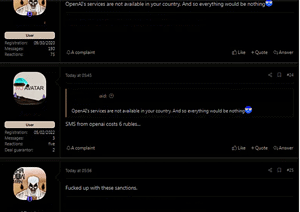
Hackers discuss on the dark web
It's not particularly difficult to bypass OpenAI's country-specific restrictions to gain access to ChatGPT. At the moment, security researchers see that Russian hackers are already discussing and checking how to bypass geofencing to use ChatGPT for malicious purposes. Check Point Research believes these hackers will attempt to implement ChatGPT into their daily criminal operations and test its capabilities. Cyber criminals are increasingly interested in ChatGPT as the AI technology behind it can help a hacker save money.
🔎 1.A hacker asks what is the best way to use a stolen payment card to pay for an upgraded account on OpenAI that gives access to more powerful and specialized models and features.
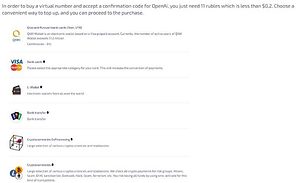
🔎 3. In general, there are many guides in Russian semi-legal online SMS services showing how to register in ChatGPT. Check Point has examples of this already being used.
No big danger yet
“In the short term, we don't believe that this new AI technology will turn the entire threat landscape upside down, but rather lead to an increase in mass-produced malware and, most importantly, much better-crafted phishing emails. Over the long term, however, integrating and improving this AI technology can completely and for the worse change the way hackers build and unleash their cyber threats on users.” — Sergey Shykevich, Threat Intelligence Group Manager at Check Point Software Technologies.
More at CheckPoint.com
About check point Check Point Software Technologies GmbH (www.checkpoint.com/de) is a leading provider of cybersecurity solutions for public administrations and companies worldwide. The solutions protect customers from cyberattacks with an industry leading detection rate for malware, ransomware and other types of attacks. Check Point offers a multi-level security architecture that protects company information in cloud environments, networks and on mobile devices, as well as the most comprehensive and intuitive “one point of control” security management system. Check Point protects over 100.000 businesses of all sizes.