
Nefilim ransomware specifically targets victims with over $ 1 billion in annual sales. Trend Micro study analyzes one of the most successful threat groups for modern ransomware.
Trend Micro, one of the world's leading providers of cybersecurity solutions, has published a case study on the ransomware group Nefilim, which provides an in-depth look at how modern ransomware attacks work. The study provides valuable background on how ransomware groups develop, act underground and how advanced detection and response platforms contribute to their defense.
How modern ransomware families operate
The approach of modern ransomware families makes it much more difficult to identify and combat cyber attacks (detection and response) for already overloaded SOC (Security Operations Center) and IT security teams. This is not only crucial for business success and corporate reputation, but also for the stress level of the SOC teams themselves.
“Modern ransomware attacks are extremely targeted, adaptable and covert, and they proceed according to tried and tested approaches that have already been perfected by APT (Advanced Persistent Threat) groups. By stealing data and locking important systems, groups like Nefilim are trying to blackmail highly profitable, global companies, ”explains Richard Werner, Business Consultant at Trend Micro. "Our latest study is a must for anyone in the industry who wants to fully understand this rapidly growing shadow economy and also want to understand how Extended Detection and Response (XDR) solutions can help tackle it."
Under the microscope: 16 ransomware groups
Among the 2020 ransomware groups examined from March 2021 to January 16, Conti, Doppelpaymer, Egregor and REvil were the front runners in terms of the number of victims at risk. Cl0p had the most stolen data hosted online at 5 terabytes (TB).
However, due to its strict focus on companies with annual sales of more than one billion US dollars, Nefilim achieved the highest average sales with extortion.
As the Trend Micro study shows, a Nefilim attack usually has the following phases
- Introductory access that misuses weak credentials for exposed Remote Desktop Protocol (RDP) services or other outward HTTP services.
- Once intruded, legitimate lateral movement admin tools are used to identify valuable systems for data theft as well as encryption.
- A "call home system" is set up with Cobalt Strike and protocols such as HTTP, HTTPS and DNS, which can pass through any firewall.
- Specially secured, so-called "bulletproof" services are used for C&C servers.
- The data is extracted and then published on Tor-protected websites in order to blackmail the victims. Last year, Nefilim released about two terabytes of data.
- The ransomware component is triggered manually as soon as enough data is available.
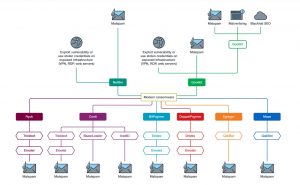
Study Findings: Relationships between malware loaders and the latest ransomware payload (Image: Trend Micro).
Trend Micro already warned of the widespread use of legitimate tools such as AdFind, Cobalt Strike, Mimikatz, Process Hacker, PsExec and MegaSync, which ransomware attackers can use to achieve their goal and go unnoticed in the process. This can make it a challenge for SOC analysts looking at event logs from different parts of the environment to understand the big picture and attacks.
Challenge for SOC analysts
Trend Micro Vision One monitors and correlates suspicious behavior across layers, from endpoints to email, servers and cloud workloads to ensure there are no backdoors for threat actors. This ensures faster response times in the event of incidents. Teams can usually stop attacks before they have a serious impact on the company.
The full report "Modern Ransomware's Double Extortion Tactics and How to Protect Enterprises Against Them" is available online from Trend Micro.
More at TrendMicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.
