LockBit, currently the most active ransomware group, expanded its activities to macOS devices in April. Furthermore, vulnerabilities in the PaperCut printer software are actively exploited. Vice Society and Play, who like to attack the education sector, have developed new methods. A brief overview of the detected threats in April.
Precisely because the Mac ecosystem has traditionally been almost ransomware-free, LockBit's new macOS ransomware is a dangerous development in the threat landscape. The new actions show that LockBit is further diversifying its operations and is currently actively developing a malware for macOS. The variant targeting the arm64 architecture of macOS first appeared on VirusTotal in November and December 2022, but went unnoticed until the end of April 2023.
LockBit encryptor in test phase
So far, however, the LockBit macOS samples analyzed by Malwarebytes appear to be harmless. The malware uses an invalid signature and is afflicted with bugs such as buffer overflows, which lead to a premature termination when running under macOS. "In its current form, the LockBit encryptor doesn't seem very mature," said Thomas Reed, director of Mac and Mobile Platforms at Malwarebytes. "However, its actual functionality could improve in the future - depending on how promising future tests turn out to be."
According to Malwarebytes, LockBit's work on a macOS ransomware variant could be a sign of more ransomware coming to the Mac ecosystem in the future.
Cl0p exploits vulnerabilities in the PaperCut printer software
The Russian hacker group Cl0p, which became known in March for exploiting a zero-day vulnerability in GoAnywhere MFT and a total of 104 attacks, was identified by Microsoft in April as exploiting critical vulnerabilities in PaperCut to steal company data.
PaperCut is print management software that was attacked by both Cl0p and LockBit in April. Two severe vulnerabilities were exploited: one that allows remote code execution (CVE-2023-27350) and one that allows information disclosure (CVE-2023-27351). Cl0p members used the TrueBot malware and a Cobalt Strike beacon to sneak through the network and steal data. Otherwise, the ransomware gang largely withdrew with only four attacks in April.
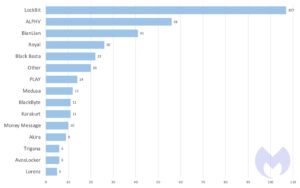
According to the analysis by the Malwarebytes Threat Intelligence team, LockBit was once again the most active ransomware group in April 2023. She reported a total of 107 victims on her dark web leak website. This is followed by ALPHV with 56 victims, BianLian with 41 victims, Royal with 26 victims and Black Basta with 22 victims.
Vice Society and Play develop sophisticated methods
The ransomware group Vice Society, known for its attacks on the education sector, recently published a PowerShell script for automated data theft. The data exfiltration tool discovered by Palo Alto Networks Unit 42 cleverly uses LotL (living-off-the-land) techniques to avoid detection.
Separately, ransomware group Play has developed two sophisticated .NET tools to make their cyberattacks even more effective: Grixba and VSS Copying Tool. Grixba scans antivirus programs, EDR suites, and backup tools to effectively plan the next steps of an attack. VSS Copying Tool bypasses Windows Volume Shadow Copy Service (VSS) to steal files from system snapshots and backups. Both tools are developed using Costura .NET development tool to allow easy installation on potential victims' systems.
As Vice Society, Play, and other ransomware groups use increasingly sophisticated LotL methods and sophisticated tools like Grixba, it becomes increasingly critical for organizations and their defense strategy to be able to proactively detect both malicious tools and the malicious use of legitimate tools within a network.
Do you have a moment?
Take a few minutes for our 2023 user survey and help make B2B-CYBER-SECURITY.de better!You only have to answer 10 questions and you have an immediate chance to win prizes from Kaspersky, ESET and Bitdefender.
Here you go directly to the survey
Countries: Germany is the third most affected
The US also tops the list of countries most affected by ransomware in April with 170 known attacks, followed by Canada with 19 attacks. Germany follows in third place with 15 known attacks in April.
Across industries, the service sector remains the top target for ransomware attacks, with 77 known victims. Both the healthcare and education sectors saw strong increases in April: the education sector saw the highest number of attacks (20) since January 2023 and the healthcare sector also saw the highest number of attacks (37) this year.
New ransomware group Akira
Akira is a new ransomware group that has been attacking companies worldwide since March 2023. In April alone, the group published data from attacks on nine companies in various sectors such as education, finance and manufacturing. Once the ransomware runs, it deletes Windows Shadow Volume Copies, encrypts files and appends the .akira file extension to the latter. Like most ransomware gangs, Akira steals company data and then encrypts it to enable a double racket. So far, data ranging from 5,9 GB to 259 GB has been published on Akira's leak website.
Akira demands ransoms ranging from $200.000 to millions of dollars - and seems willing to lower ransom demands for companies that just want to prevent the disclosure of Akira's stolen data but don't need a decryptor.
New ransomware group Trigona
The Trigona ransomware group first appeared in October 2022 and has been targeting various industries worldwide ever since. In April, six attacks by the group became known. Attackers use tools like NetScan, Splashtop, and Mimikatz to gain access and collect sensitive information from the targeted systems. In addition, they use batch scripts to create new user accounts, disable security features, and cover their tracks.
MoneyMessage ransomware
Money Message is a new ransomware that attacks both Windows and Linux systems using advanced encryption techniques. In April, cybercriminals used Money Message ransomware to target at least XNUMX victims. The criminals also targeted some large companies worth billions of dollars, such as the Taiwanese computer hardware manufacturer MSI (Micro-Star International).
More at Malwarebytes.com
Via Malwarebytes Malwarebytes protects home users and businesses from dangerous threats, ransomware and exploits that are undetected by antivirus programs. Malwarebytes completely replaces other antivirus solutions in order to avert modern cybersecurity threats for private users and companies. More than 60.000 companies and millions of users trust Malwarebyte's innovative machine learning solutions and its security researchers to avert emerging threats and eliminate malware that antiquated security solutions fail to detect. You can find more information at www.malwarebytes.com.