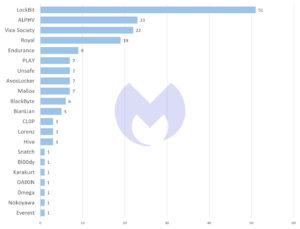
It's not good news from the February Malwarebytes ransomware report: LockBit is back at number 1. As in 2022, the ransomware group again tops the list of groups selling ransomware-as-a-service (RaaS) in 2023.
Malwarebytes' threat intelligence team attributed 51 attacks to LockBit in January (up from 55 attacks in December 2022). In second place is ALPHV with 23 attacks, closely followed by Vice Society with 22 and Royal with 19 attacks.
Ransomware: USA most commonly affected
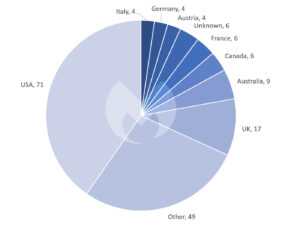
When it comes to the distribution of ransomware attacks by country, the USA is again by far the most common target in January 2023 with 71 attacks. In Europe, the following countries were affected: the United Kingdom with 17 attacks, France with six attacks, and Germany, Austria and Italy with four attacks each.
Industries: Targeting the education sector
In terms of industries, the service sector stands out with 53 attacks and the education sector with 21 attacks in January 2023. The ransomware group Vice Society alone published the data from nine schools on its leak page in January. Vice Society is believed to be a Russia-based group whose preferred targets are universities and schools. It may therefore not be coincidental that attacks on the education sector are at their highest level in three months.
LockBit: Conti source code exploited
In January, LockBit made a name for itself with its new encryption program "LockBit Green", which is based on the previously leaked source code of the Conti ransomware. This new ransomware version — third in the group after LockBit Red (aka LockBit 2.0) and LockBit Black (aka LockBit 3.0) — shares 89 percent of its code with Conti Ransomware V3 and has been used in at least five attacks .
Considering LockBit's success, Malwarebytes says it's still unclear why the group is offering a new variant of its ransomware. A possible explanation could be that it wants to attract affiliates who are more comfortable with Conti-based ransomware, such as former Conti members. In this case, the new ransomware version could be seen as a marketing activity.
Black Basta: No activity in January
Black Basta is conspicuous by its absence in January. No information from the ransomware group was published on the leak pages on the dark web. The Malwarebytes Threat Intelligence team has been tracking the group since April 2022. Since then, the ransomware has appeared in the Malwarebytes team's rankings based on known attacks.
However, one thing is also certain: only companies that have not paid a ransom are displayed on the leak sites on the Darknet. An extremely successful month for the ransomware group could therefore also seem like an inactive month. However, according to Malwarebytes, a month without anyone refusing to pay would be very unusual.
Additionally, Black Basta's Tor website, where new victims are posted, has been down for several weeks. Malwarebytes observed that the site was reactivated on January 22nd, but was already offline again on January 23rd. The backend of the site, which is used to contact the victims, also appears to have failed.
Hive: Hacker network dismantled in January
The global hacker network Hive was smashed by authorities from Germany and the USA in January. The ransomware group was no stranger to Malwarebytes either: in 2022 it was one of the most used RaaS. Malwarebytes has been aware of 2022 attacks by the group since April 120. It ranks fifth after LockBit, ALPHV, Black Basta and Conti.
In January, Malwarebytes was able to attribute three attacks to the group, after 15 attacks in December 2022. The hacker network was then broken up at the end of January. The US Department of Justice announced the success of a months-long campaign of disruption.
Europol, FBI and police success against Hive
Investigators have reportedly had access to Hive's computer networks and infrastructure since July 2022 thanks to the campaign. The access became known on January 26, when a notice appeared on the hackers' website on the dark web that the site had been confiscated.
According to authorities in Germany and the US, the ransomware group had targeted more than 1.500 organizations in over 80 countries, including hospitals, school districts, financial companies and critical infrastructure, and attempted to collect more than $100 million in ransom payments from its victims to blackmail.
More at Malwarebytes.com
Via Malwarebytes Malwarebytes protects home users and businesses from dangerous threats, ransomware and exploits that are undetected by antivirus programs. Malwarebytes completely replaces other antivirus solutions in order to avert modern cybersecurity threats for private users and companies. More than 60.000 companies and millions of users trust Malwarebyte's innovative machine learning solutions and its security researchers to avert emerging threats and eliminate malware that antiquated security solutions fail to detect. You can find more information at www.malwarebytes.com.