
The QakBot malware harbors a high security risk due to the often low detection rate. QakBot is distributed through XLSB files, making it difficult to spot.
Qakbot is not new to malware, but the Hornetsecurity Security Lab is now warning of a new type of distribution: IT security experts have discovered that XLM macros are used in XLSB documents to distribute QakBot malware. Since both XLM macros and the XLSB document format are uncommon, these new malicious documents have a very low detection rate by current anti-virus solutions.
What is QakBot?
QakBot (also known as QBot, QuakBot, Pinkslipbot) has been around since 2008. The malware is distributed via Emotet by Emotet downloading the QakBot loader from infected victims. QakBot is also distributed directly via email. For this purpose, e-mail conversation thread hijacking is used in the campaigns - i.e. e-mails that are found in the mailboxes of the victims are replied to. QakBot is also known to escalate attacks by downloading the ProLock ransomware.
Why are the attacks not recognized?
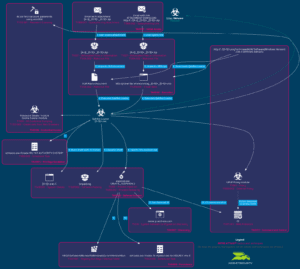
Sequence of a QakBot attack via XLM macros in XLSB documents. Info: Hornetsecurity Security Labs (click to enlarge)
XLSB is a binary Excel workbook format, the main purpose of which is to make reading and writing to the file faster and to reduce the size of very complex spreadsheets. However, with current computing power and memory availability, the need for this binary format has decreased and is rarely used today.
According to the experts at the Hornetsecurity Security Lab, the combination with the old and also not very frequently recognized XLM macros means that the current documents are not identified as harmful by any of the antivirus solutions listed on VirusTotal.
Camouflaged in a ZIP file
The QakBot XLSB files are distributed in an attached ZIP file. This ZIP file contains the XLSB document which, when opened, pretends to be a DocuSign encrypted document. The user must "Enable Editing" and "Enable Content" to decrypt it.
The URL is composed using the XLM macro and simulates the download of a PNG file.
In reality, however, the PNG file is the QakBot loader's executable file.
What can be done about this attack method?
- Most antivirus solutions focus on modern VBA macro malware, but often fail to detect re-emerging old and now less common XLM macros and XLSB documents.
- Companies should therefore rely on advanced security services that are able to react to new threats and attack methods in the shortest possible time.
The security experts from the Hornetsecurity Security Lab provide a detailed analysis of this attack method on their blog.
More on this at HornetSecurity.com
About Hornetsecurity Hornetsecurity is the leading German cloud security provider for e-mail in Europe and protects the IT infrastructure, digital communication and data of companies and organizations of all sizes. The security specialist from Hanover provides its services via 10 redundantly secured data centers around the world. The product portfolio includes all important areas of e-mail security, from spam and virus filters to legally compliant archiving and encryption, to defense against CEO fraud and ransomware. Hornetsecurity has around 200 employees at 12 locations around the world and operates with its international dealer network in more than 30 countries.
