Phishing is usually only explained theoretically. Kaspersky experts explain an attack using a live example. An in-depth look at a phishing website and its attempts to disguise itself as an email scanner and use it to lure victims.
In recent years, there has been a fairly regular news of email-based infections of corporate networks (and ransomware in general). It is therefore no surprise that fraudsters like to use the fear of such attacks to gain access to email credentials for company accounts by tricking company employees into "scanning" their mailboxes.
The trick is aimed at people who are aware of the potential threat posed by malware in email but do not know how to deal with it. In any case, the IT security team should explain the fraudsters' tricks to the employees and use examples to illustrate what employees should pay attention to in order not to fall victim to cyber criminals.
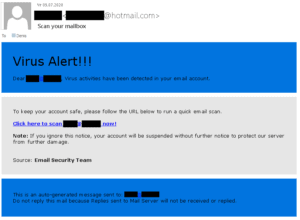
The disguised phishing email
This fraudulent message uses the tried and true trick of victim intimidation. You can see signs directly in the header: Subject “Virus alert” followed by three exclamation marks. As insignificant as the punctuation may seem, it is arguably the first thing that should give the recipient an indication that something may be wrong. Unnecessary punctuation in a work email is a sign of drama or unprofessionalism. Either way, it is very inadequate for a notification trying to protect you from a threat.
Every recipient should first ask themselves who sent the message in the first place. The email states that if the recipient does not take any action, the account will be blocked. It would be logical to assume that it was sent either by the IT service who runs support for the company's mail server or by employees of the mail service provider.
Where the infection then takes place
It should be noted, however, that no provider or internal service would require action on the part of the user to scan the contents of the inbox. Scanning takes place automatically on the mail server. Also, “virus activity” is rare within an account. Even if someone sent a virus, the recipient would have to download and run it. The infection takes place on the computer, not in the email account.
To come back to the first question: A look at the sender should ring two alarm bells. First, the email was sent from a Hotmail account, while a legitimate notification shows the company's or provider's domain. Second, the message should come from the "email security team". If the recipient's company uses a third-party provider, their name must appear in the signature. And if the mail server is in the company's infrastructure, the notification comes from the in-house IT team or the IT security service. It is very unlikely that an entire team would be solely responsible for email security.
Hidden urls in the link
Next the link. Most modern email clients display the URL hidden behind the hyperlink. If the recipient is asked to click through to an email scanner that is hosted on a domain that neither your company nor the mail provider owns, it is almost certainly phishing.
The website looks like some kind of online email scanner. To give the impression of authenticity, it displays the logos of a number of antivirus providers. In the header there is even the name of the recipient's company, which should dispel any doubts as to whose tool it is. The website will first simulate a scan and then pause it with the unusual message "Please verify your account below to complete the email scan and delete all infected files". The account password is of course required for this.
Phishing website
To determine the true nature of a website, first examine the contents of the browser's address bar. First, as mentioned, it is not the right domain. Second, the URL most likely contains the recipient's email address. That is fine in and of itself - the user ID could have been passed through the URL. However, if there is any doubt about the legitimacy of the site, replace the address with whatever characters you want (but keep the @ symbol to keep the look and feel of an email address).
Websites of this type use the address provided via the link in the phishing email to fill in the blanks in the website template. For experimental purposes we used the non-existent address [email protected], and the site duly replaced “yourcompany” in the name of the scanner and the entire address in the name of the account, after which it apparently began scanning non-existent attachments in non-existent emails. When we repeated the experiment with a different address, we found that the attachment names were the same in each "scan".
The fake website simulates a scan
Another contradiction is shown in that the scanner supposedly scans the contents of the mailbox without authentication. Then why does he need the password? But there are ways and means to protect your employees.
Kaspersky has carefully analyzed the signs of phishing both in the email and on the website of the fake scanner. Simply showing this post to employees will give them a rough idea of what to look out for. But that's just the tip of the proverbial iceberg. Some fake emails are more sophisticated and more difficult to debunk.
Kaspersky therefore recommends that employees be continuously aware of the latest cyber threats - for example with our Kaspersky Automated Security Awareness Platform.
In addition, use security solutions that are able to detect phishing e-mails on the mail server and prevent work computers from being forwarded to phishing sites. Kaspersky Security for Business can do both. In addition, we offer a solution that extends the integrated protection mechanisms of Microsoft Office 365.
More on this in the blog at Kaspersky.com
About Kaspersky Kaspersky is an international cybersecurity company founded in 1997. Kaspersky's in-depth threat intelligence and security expertise serve as the basis for innovative security solutions and services to protect companies, critical infrastructures, governments and private users worldwide. The company's comprehensive security portfolio includes leading endpoint protection as well as a range of specialized security solutions and services to defend against complex and evolving cyber threats. Kaspersky technologies protect over 400 million users and 250.000 corporate customers. More information about Kaspersky can be found at www.kaspersky.com/