Just as cyber criminals have exploited the pandemic with corona-related phishing attacks, they are now trying to abuse the vaccine issue to steal money and personal information.
The FBI issued a warning about emerging fraud attempts related to COVID-19 vaccines back in December. A Barracuda analysis conducted between October 2020 and January 2021 found that hackers are increasingly using vaccine-related emails in their targeted spear phishing attacks.
Attack increase since November 2020
After pharmaceutical companies like Pfizer and Moderna announced the availability of vaccines in November 2020, the number of vaccine-related phishing attacks rose by 12 percent. By late January, the average number of vaccine-related spear phishing attacks had increased 26 percent since October. The number flattened out over the holidays, as is typically the case with corporate attacks.
While most of the vaccine-related phishing attacks analyzed were fraudulent, there were two predominant types of spear phishing attacks using vaccine-related themes: branded impersonation attacks and compromise of business emails.
Brand impersonation attacks
Cyber criminals used vaccine-related phishing emails to impersonate a well-known brand or organization. The messages contained a link to a phishing website promoting early access to vaccines, offering vaccines for a fee, or even posing as a healthcare professional requesting personal information to verify eligibility for a vaccine.
Business email compromise
Attackers use Business Email Compromise (BEC) to impersonate people within an organization or their business partners. In the past few years, it has been one of the most harmful email threats, costing businesses over $ 26 billion. Recently, these very targeted attacks have centered on vaccine-related issues. Barracuda uncovered attacks in which cybercriminals posed as employees who need an urgent favor while getting vaccinated or as a human resources specialist who announced that the company had secured the vaccines for its employees.
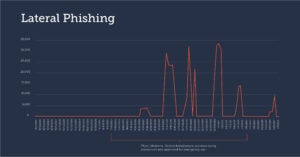
Misuse of hijacked accounts
Cyber criminals use phishing attacks to compromise and hijack business accounts. Once inside the company, sophisticated hackers conduct intelligence activities before launching targeted attacks. Most of the time, they use these legitimate accounts to send bulk phishing and spam campaigns to as many people as possible before their activity is detected and an account locks them out.
Barracuda not only has visibility into email messages coming from outside the organization, but also internal communications. As a result, it is possible to trace fraudulent messages that are sent internally - usually from compromised accounts. The research found that lateral vaccine-related phishing attacks were increasing at the same time that key COVID-19 vaccines were announced and approved worldwide.
Protective measures against vaccine-related phishing
1. Skepticism about all vaccine-related emails
Some email scams include offers to get the COVID-19 vaccine early, put yourself on a waiting list, or have the vaccine sent direct to you. Users should not click links or open attachments in these emails as they are typically malicious.
2. Use of artificial intelligence
Scammers are adapting their email tactics to bypass gateways and spam filters. It is therefore important to have a security solution that detects and protects against spear phishing attacks, including branded impersonation attacks, compromising business emails, and taking over email accounts. Organizations should employ specially designed technology that doesn't rely on just looking for malicious links or attachments. Using machine learning to analyze normal communication patterns across the organization, the solution can identify anomalies that could indicate an attack.
3. Account transfer protection
Organizations shouldn't focus their protections on external email messages alone. Some of the most devastating and successful spear phishing attacks involve compromised internal accounts. Therefore, it should be ensured that fraudsters do not use the company as a base for these attacks. Again, we recommend technology that uses artificial intelligence to detect when accounts have been compromised and remedies in real time by alerting users and removing malicious emails sent from compromised accounts.
4. Employee training to identify and report attacks
Organizations should provide up-to-date training to employees on phishing related vaccinations, seasonal scams, and other potential threats. It should be ensured that employees can identify the latest attacks and know how to report them immediately to the IT department. The use of phishing simulations for e-mail, voicemail and SMS is also recommended in order to train users to detect cyberattacks, to test the effectiveness of the training courses and to identify the most vulnerable users.
5. Strong internal fraud prevention policies
Companies should establish guidelines for the correct handling of personal and financial information and review them regularly. You can help your employees avoid costly mistakes by establishing procedures to confirm all email requests for transfers and payment changes. All financial transactions should require multiple personal or telephone confirmation and / or approval.
The flood of new phishing campaigns will not level off in the near future either. However, with the above measures, organizations can build a strong, layered defense consisting of employee training and security technology to significantly mitigate the risk of these attacks.
More at Barracuda.com[starboxid=5]