
Kaspersky have discovered the third case of a UEFI firmware bootkit “in the wild”. The MoonBounce bootkit is more elusive and persistent than its predecessors. The campaign is credited to well-known Chinese-speaking Advanced Persistent Threat (APT) actor APT41.
Kaspersky's security experts have discovered another firmware boot kit [1]. The malicious implant, dubbed 'MoonBounce', is hidden in computers' Unified Extensible Firmware Interface (UEFI) firmware – an essential part of computers. This is located in the SPI Flash, a memory component outside of the hard disk. Such implants are notoriously difficult to remove and have limited visibility for security products.
UEFI firmware bootkit partially invisible
MoonBounce first emerged “in the wild” in Spring 2021, demonstrating a sophisticated attack flow that represents a significant advance over previously reported UEFI firmware bootkits. The campaign is almost certainly attributed to well-known Advanced Persistent Threat (APT) actor APT41.
UEFI firmware is an important component in most computers. Your code is responsible for booting up the device and handing control over to the software to load the operating system. This is located in the so-called SPI flash, a memory outside of the hard disk. If that firmware contains malicious code, it will launch before the operating system, making malware implanted through a firmware bootkit particularly difficult to erase. It cannot be removed simply by reformatting a hard drive or reinstalling an operating system. Because the code resides outside of the hard drive, the activities of such bootkits go undetected by most security solutions unless they have a feature that specifically scans that part of the device.
MoonBounce: Modified Bootkit
MoonBounce is only the third identified UEFI bootkit. It appeared “in the wild” in Spring 2021 and was first discovered by Kaspersky researchers when they were investigating the activity of their firmware scanner [2], which has been included in Kaspersky products since early 2019. This is specifically designed to detect threats hiding in ROM-BIOS, including UEFI firmware images. Compared to the two previously discovered bootkits LoJax [3] and MosaicRegressor [4], MoonBounce shows significant progress with a more complicated attack flow and greater technical sophistication.
The implant resides in the CORE_DXE component of the firmware, which is already invoked during the UEFI boot sequence. The implant's components then enter the operating system via a series of hooks that intercept certain functions, where they contact a command-and-control server to fetch more malicious payloads that Kaspersky was unable to fetch. The infection chain itself leaves no traces on the hard drive, since its components work in memory, enabling a fileless attack that leaves little trace.
Expanded threat arsenal
Investigating MoonBounce, Kaspersky experts detected various malicious loaders and post-exploitation malware across multiple nodes of the same network. This includes
- ScrambleCross or Sidewalk, an in-memory implant that can communicate with a C2 server to exchange information and run additional plugins,
- Mimikatz_ssp, a publicly available post-exploitation tool used to harvest credentials and sensitive data,
- a previously unknown Golang-based backdoor
- and Microcin [5], a malware typically used by threat actor SixLittleMonkeys.
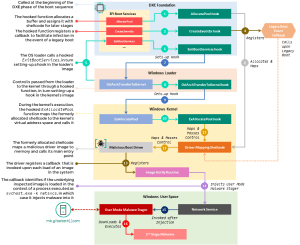
Flow of the MoonBounce execution from the start sequence to the malware deployment in the user area (Image: Kaspersky).
It could be that MoonBounce downloads these types of malware, or a previous infection by one of these malware variants is used to compromise the computer to allow MoonBounce to gain a foothold on the network. Another possible method of infection for MoonBounce would be that the computer was compromised before delivery to the notified company.
Infected PCs before delivery
In both cases, the assumption is that the infection happens by remotely accessing the target computer. While LoJax and MosaicRegressor add DXE drivers, MoonBounce modifies an existing firmware component to allow for a more subtle and stealthy attack.
As part of the overall campaign against the network in question, the attackers apparently performed a variety of actions, such as archiving files and gathering network information. The commands used by the cyber criminals indicate that they were interested in lateral movement and data exfiltration. Since a UEFI implant was used, it is likely that they should be engaged in spying activities.
Attack points to group APT41
According to Kaspersky, MoonBounce can be attributed with a high degree of certainty to APT41 [6], a Chinese-speaking threat actor that has been conducting cyberespionage and cybercrime campaigns worldwide since at least 2012. Furthermore, the existence of some of the above malicious programs on the same network indicates a possible connection between APT41 and other Chinese-speaking threat actors.
So far, the firmware bootkit has only been discovered on a single computer from a holding company in the high-tech market. However, other associated malicious programs - such as ScrambleCross and its loaders - were found on the networks of several other victims.
"While we cannot positively link the additional malware implants found during our investigation to MoonBounce, it appears that some Chinese-speaking threat actors share tools with each other to support their various campaigns," comments Denis Legezo, Senior Security Researcher in the Global Research and Analysis Team (GreAT) at Kaspersky. "In particular, there appears to be a connection between Moon Bounce and Microcin."
Close relationship with MosaicRegressor
"Perhaps more importantly, this new UEFI bootkit is similarly advanced to MosaicRegressor, which we reported on in 2020," said Mark Lechtik, Senior Security Researcher in Kaspersky's Global Research and Analysis Team. “Transforming a previously benign firmware component into one that is now easier to access by malware on the system is an innovation not seen in previous comparable firmware bootkits. This makes digital infections much more difficult to identify. As early as 2018, we predicted that UEFI threats would take up more space in the future - this trend seems to be confirmed. We wouldn't be surprised if more bootkits popped up in 2022. Fortunately, manufacturers have started paying more attention to firmware attacks, and so more security technologies like BootGuard and Trusted Platform Modules are gradually being introduced.”
More at kaspersky.com
About Kaspersky Kaspersky is an international cybersecurity company founded in 1997. Kaspersky's in-depth threat intelligence and security expertise serve as the basis for innovative security solutions and services to protect companies, critical infrastructures, governments and private users worldwide. The company's comprehensive security portfolio includes leading endpoint protection as well as a range of specialized security solutions and services to defend against complex and evolving cyber threats. Kaspersky technologies protect over 400 million users and 250.000 corporate customers. More information about Kaspersky can be found at www.kaspersky.com/
