
Secondary storage IT has to face three challenges: Complexity, durability and security. Three concerns, one solution: Managed Storage - a perfect interplay of hardware, software and service.
The great complexity in companies as well as in the IT infrastructure runs counter to data backup. The amount of data, different data types and different authorizations keep the complexity growing and present IT officers with the challenge of using all systems equally and secure against attacks in the long term to have to.
starting position
The complexity carries over to the Lifespan. Which system has which lifespan? How can you ensure that you do not lose data even if data is being migrated while others are still running? These aspects have a major impact on data backup.
Managed storage is the perfect interplay of hardware, software and service from a single source, one simplification generated that longevity increases and is explicitly about the Safety takes care.
Challenge 1: complexity
Sources such as virtual machines, filers, SaaS, mobile devices and (remote) work stations have to be secured on the one hand, and on the other hand pose a threat to data security. The complexity of the various areas requires a precise and individual consideration of the systems in order to identify be able, which device needs which security and what software can be used for this. In addition, many companies still work with different software solutions because, for example, old backup solutions have not yet been integrated into the new solutions or can no longer be mapped.
It is backed up to different target areas, such as disc storage, network disc storage, local disc storage, USB disks or cloud storage. the The amount of data increases enormously and, depending on the performance requirements, also the complexity. With every available hardware, another SLA comes into play with maintenance contracts and user interfaces that have to be operated and updated.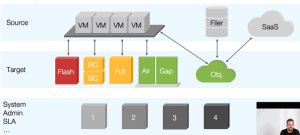
Challenge 2: longevity
In the area of (audit-proof) long-term archiving, there is another point in the secondary storage area: longevity. Audit-proof data with legal requirements must be verifiably stored unchangeably. In order not to have to migrate these regularly and move them back and forth between storage systems, a storage system is required that has a longer maintenance guarantee than the classic three or five years.
In addition to longevity, special software solutions require an interface that can be operated for a long time and that supports both old and new systems and keeps them secure. Also permanent Updates to the systems, addressing security vulnerabilities and concerns are paramount.
Longevity doesn't just mean having a system waited a long time can be. It also means that the software lives on Hardware remains available with a guarantee of replacement and the system takes care of itself. It prevents data loss and ensures its own longevity itself - possibly even with an optional "worming". Longevity also means that the system expands and moves with the company be scaled can, and that the Security steadily expanded can be.
Challenge 3: Security
The security decreases with the growing Complexity of the system. The more devices are used, the more systems are run in parallel, the more attack surfaces or attack potential the overall solution has - and of course at the expense of security.
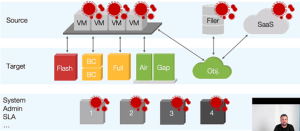
As can be seen in the picture example, every source is vulnerable. Coupled with different hardware components, software versions, operating systems and security gaps, the rate increases Vulnerability of the entire system exponentially. The SLA, administration and maintenance status also play an important role here. The higher the complexity, the more vulnerable the system is.
Important: 59% of IT attacks also target the cloud. Attacks and ransomware often focus on the backup first and then encrypt the rest. Even in cloud storage, attackers can remove all pillars and encrypt it.
The Silent Bricks System as a solution in managed storage:
FAST LTA offers with the Silent Bricks a system that simplification generated that longevity increases and is explicitly about the Safety takes care. This is implemented by our Managed storage, the interaction of hardware, software and service.
Here the software is tailored to the hardware, and the hardware is tailored to the respective application. FAST LTA follows the approach of longevity: All hardware components are made by FAST LTA designed, manufactured and manufactured in-house. In this way it can be guaranteed that all hardware components can be supplied and maintenance can be guaranteed at any time, even for systems that have been in operation for ten years or more.
The Service thought stands by FAST LTA with in first place. Unlike other providers, the customer relationship begins with FAST LTA only really after the sale of the system, because from that moment on we take over Responsibility and service for the product. This is only possible because hardware, software and service come from a single source. Our solutions are innovative and modern, reduce the overall complexity of the storage and monitor themselves.
Managed storage explained in detail? René Weber will take care of that for you. See you just watch the video.
Or get to know the Silent Brick System personally. In our free webinar IT manager Thorsten Staude presents the unique backup solution with all possible uses in detail.
More at FASTLTA.com
About FAST LTA the FAST LTA is the specialist for secure secondary and long-term storage systems. The combination of durable and low-maintenance hardware, integrated software for data backup and on-site maintenance contracts with a term of up to 10 years ensure long-term, cost-effective storage of data from archive and backup applications. In-house developments such as local erasure coding, sealing using hardware WORM and efficient energy management help medium-sized customers to protect themselves against data loss through ransomware attacks and misconfiguration and to meet regulatory and legal requirements (GDPR). The Munich provider's solutions have proven themselves in thousands of installations in healthcare, public administration, film/TV/video and industry.
