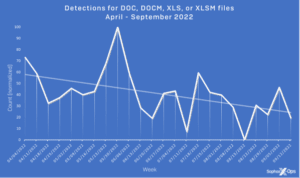
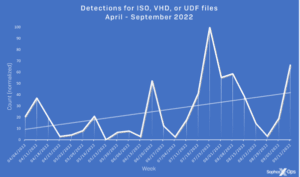
Since Microsoft announced earlier this year that it would block macros from the Internet, there has been a trend in cyber crime to use archive formats or disk images to infiltrate systems with malware. The number one gateway is still email.
In February of this year, Microsoft announced that it would block macros from the Internet by default. Such macros have been abused by attackers for years to deliver malware. While the security community speculated that attackers would switch to alternative formats because of Microsoft's decision, Sophos has already confirmed this fact with its telemetry data.
Malware: New paths via other file formats
From April to September this year, Sophos has seen a sharp drop in the number of malicious .doc, .docm, .xls and .xlsm files - four popular Office formats used to proliferate malicious macros. At the same time, there was a steady increase in the use of obscure archive formats (ACE, ARJ, XZ, GZ or LZH) up to mid-June and a sharp increase in the more common archive formats (ZIP, 7Z, CAB, TAR and RAR) from September. The use of disk image formats (ISO, VHD, and UDF) for malware distribution has also steadily increased.
Disk image formats are particularly attractive to threat actors because they bypass Microsoft's new Mark of the Web (MOTW) feature. Microsoft uses MOTW to determine whether or not a macro is from the Internet; if this is the case, it is automatically blocked.
Bypass disk image formats Check
Security products should also be able to unpack multiple archive and disk image formats, including unpopular formats, to properly scan these attachments for malware. To further mitigate the risks, email filters can be configured to block certain file formats by default. E-mails are still one of the main attack vectors.
E-mails remain dangerous
Chester Wisniewski, Principal Research Scientist at Sophos, says: “We've been giving the same advice on email security for years. Things like 'don't click on this link' or 'don't open dangerous attachments'. The reality is that the cybersecurity landscape is constantly changing. It is unlikely that cyber criminals will abandon macros entirely, as they are highly likely to adapt to these latest Microsoft security measures. Businesses should do the same. Good email security needs to be managed centrally, with security teams focusing on the technical aspects, e.g. B. which file extensions are dangerous. It is also important to educate users on how to avoid falling for the tricky social engineering of cybercriminals.”
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.