The experts at Bitdefender Labs report an initial assessment of Log4j and Log4Shell: Hackers are intensively looking for vulnerabilities. A Tor concealment of the accesses to real endpoints makes Germany the seemingly number one country of origin of the attacks. Bitdefender counted 36.000 hits on honeypots in seven days.
The Log4Shell vulnerability has been actively exploited by Apache as CVE-9-2021 since it was disclosed on December 2021, 44228. The results are amazing. Most of the attack attempts seem to come from western industrialized countries such as Germany, the USA and the Netherlands, but apparently some of them hide their origin behind exit nodes of the Tor network. This suggests that the attackers are actually operating from other countries. Almost every second victim worldwide is in the United States. That's what the data analysis of Bitdefender Labs Honeypots and Bitdefender Telemetry of several 100 million endpoints shows from December 9th to December 16th. Bitdefender is currently seeing a high level of interest in the new attack options on the Darknet.
There is also a dynamic threat situation and an active hacker scene
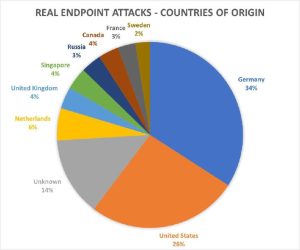
Country of origin of the Log4Shell attacks on real endpoints - Bitdefender telemetry data (Image: Bitdefender).
Since it will take months to fix the vulnerability or even to understand the extent of the threat, the hackers now have a large window of time to exploit the vulnerability. Bitdefender Labs have not yet discovered any activities by known ransomware-as-a-service gangs or APT backers. But many are looking for ways to set foot in the networks now in order to become active later. Bitdefender expects that professional attackers will use this loophole as the first vehicle for their long-term attacks on highly relevant targets. After that, they will secretly close the chess point in order to exclude other attackers and to hide their intrusion from the defense scan. The attacks will come when the storm subsides. The attackers will presumably wait until Christmas or the turn of the year with their actual attacks.
Where did the attacks come from?
According to telemetry data, most attacks on real endpoints seem to originate in Germany (34%), ahead of the USA (26%) (Figure 1). Here, however, the concealment of the original location via the Tor network must be taken into account.
With the 36.000 honeypot attacks counted in the last seven days, a different picture emerges: Here the attacks come most frequently from the USA (21%). Behind are India (20%), Germany and Hong Kong with 12% each - closely followed by China (10%) and Russia (9%) (Figure 2).
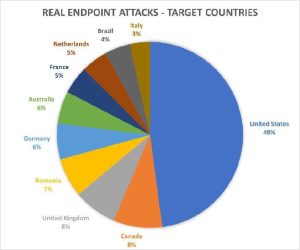
Almost every second network attacked is in the US (48%), followed by Canada and the UK (8% each) and Romania (7%), according to Bitdefender telemetry. Germany is in fifth place here with 6%. (Figure 3).
Obfuscation of origin when attacking real endpoints
The high rate of attacks allegedly originating in Germany and western industrial nations on real endpoints in Bitdefender telemetry does not result from the initially assumed reason that one-time virtual machines from Infrastructure-as-a-Service data centers are the starting point. Only a small percentage of attacks have a source address that points to cloud providers such as AWS, Azure or Google Cloud Platform (GCP). However, over 50% of the source IPs could be assigned to exit nodes of the Tor network (onion router). The hackers use a network of virtual tunnels to hide their identity and origin. When routing their attacks, they choose machines closer to the target victims as a starting point.
The threat is taken seriously
Fortunately, the analysis also showed how conscientiously and efficiently companies check their own IT and take the threat seriously. In the run-up to the telemetry analysis, the experts filtered out around 75 percent of the attacks on endpoints that were obviously started by the IT managers in order to check their own system for weak points.
Bitdefender protects against the vulnerability
Bitdefender products and services are protected against the vulnerability. Information on how to do this can be found online at Bitdefender.
More at Bitdefender.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de