The IT threat situation in Germany and the world is intensifying. Tetra Defense, an Arctic Wolf company, collects and analyzes IT security data every quarter and uses it to assess the current IT threat situation and develop countermeasures. The results from Q1 2022 (January - March).
In order to know how companies can most effectively protect themselves against cyber attacks, they need to know how attackers gain access to systems. An attacker's initial entry point is called the Root Point of Compromise (RPOC). There are three different categories:
Know where the attack is coming from
- External Attacks – A known vulnerability is used to gain access to the system.
- user action – The attacked users become active themselves and, for example, open an infected document in a phishing email.
- misconfiguration – Threat actors gain access through misconfigured systems (e.g. a web portal that is not password-protected).
Tetra Defense data shows that well over two-thirds of all attacks (82%) in the first quarter of 2022 were "external attacks", including:
- 57% via a known vulnerability in the victim's network
- 25% caused by a Remote Desktop Protocol (RDP)
Patching pays off
The evaluation showed that incidents in which the RPOC was an "external vulnerability" caused significantly higher additional costs than others. These costs can be reduced with timely installed or updated patches. Therefore, to mitigate risk from external vulnerabilities, organizations should understand their attack surface and prioritize patching based on risk, as well as ensure they have the defenses in place to protect their systems.
The danger from within: the human being
The numbers from Tetra Defense also confirm an old cybersecurity wisdom: the greatest threat in IT security is people.
- Almost a fifth (18%) of all cyber security incidents in companies can be traced back to the actions of individual employees
- More than half (54%) of these incidents were caused by opening an infected document (e.g. attachments from a spam email).
- 23% of incidents were due to compromised credentials
- Reusing the username and password combination is the trigger for the incidents in most of these cases
- To increase access security, we recommend using multi-factor authentication (MFA)
ProxyShell outperforms Log4Shell
After attracting attention in December 4, the Log4J/Log2021Shell vulnerability was only the third most exploited external threat in Q2022 22 (33% of all incidents). ProxyShell vulnerabilities (a series of Microsoft Exchange vulnerabilities) were exploited significantly more frequently (XNUMX%).
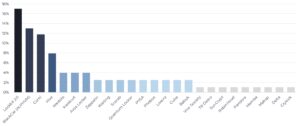
These industries are most at risk
The industry most at risk in the first quarter of 2022 was — by a wide margin — healthcare. Finance, education, manufacturing and construction followed and also faced increased threat. The service, logistics, art and energy sectors had a rather low risk of becoming the target of cyber attacks. However, especially in view of the global unrest and financial uncertainties, companies from all industries must remain vigilant.
Thanks to these quarterly evaluations, Arctic Wolf and Tetra Defense can not only share their knowledge, but also develop new detection methods and improve existing ones. Arctic Wolf works XNUMX/XNUMX alongside its customers to anticipate threat landscapes, implement new solutions and leverage threat intelligence and analytics to improve the Arctic Wolf Security Operations Cloud.
More at ArcticWolf.com
About Arctic Wolf Arctic Wolf is a global leader in security operations, providing the first cloud-native security operations platform to mitigate cyber risk. Based on threat telemetry spanning endpoint, network and cloud sources, the Arctic Wolf® Security Operations Cloud analyzes more than 1,6 trillion security events per week worldwide. It provides company-critical insights into almost all security use cases and optimizes customers' heterogeneous security solutions. The Arctic Wolf platform is used by more than 2.000 customers worldwide. It provides automated threat detection and response, enabling organizations of all sizes to set up world-class security operations at the push of a button.