IoT - the Internet of Things continues to expand. Not only does the home office contribute to this. Smart hardware is finding ever broader application possibilities. However, this also increases the area of attack and risk. Manufacturers and users are equally asked to ensure more security.
The dangers of the Internet of Things are becoming more diverse: Employees access the company network more often from home, while at the same time they use smart devices privately. This trend continues: According to analysts from BERG Insight, an annual growth of 20,2 percent is expected in Europe. This also increases the risks. Bitdefender telemetry has determined for 2020 that 23 percent of IoT security gaps were to be found in NAS storage, while 19 percent in media players, nine percent each on smart TVs and IP cameras and six percent each on There was no need for streaming devices or set-top boxes.
Customers should be able to use their devices without hesitation. Ensuring this is the task of several actors, including professional associations, authorities and the legislature. First of all, manufacturers and users themselves are asked.
Specifications for providers: raise security standards
- Developing secure solutions: There is still room for improvement when it comes to security for IoT applications. Even simple measures can significantly reduce risks. The dangers often arise from thoughtless development and a lack of transparency. The developers set up user accounts that they do not document and provide with standard passwords. Users do not know anything about this, so they do not change these settings, although the accounts remain active with all functions after commissioning. Often they are endowed with considerable rights. Cyber criminals therefore try to discover such default passwords and systematically check applications for corresponding users. For this reason, manufacturers must specify all user accounts, because this is the only way users can assign individual login data or remove them entirely. There is also another loophole: When the setup is running, applications often send unsecured login data over the network. Manufacturers could also do something about this.
- Demand safe behavior: Manufacturers can ensure that users are more careful with their own passwords. During setup you can specify that the user has to change the access data. In this way, they successfully provide more protection in a simple manner.
- Bringing updates to the man: Software should always be up to date, especially for IoT products. However, it is often too cumbersome for users to initiate updates or they do not think about it. You want to use devices and software easily without having to worry about settings. Manufacturers should therefore install updates automatically and save their customers from unpleasant work steps.
- Use standard operating systems: Standard operating systems should be used in preference. Bitdefender telemetry data shows that proprietary operating systems are responsible for 96 percent of the security flaws found. They are only used in 34 percent of the devices.
The cooperation between the manufacturer and security experts is just as crucial. Often this is also the case. But unfortunately, some companies still haven't named a contact person for security. This means that weak points cannot be eliminated so quickly.
Homework for private users and companies
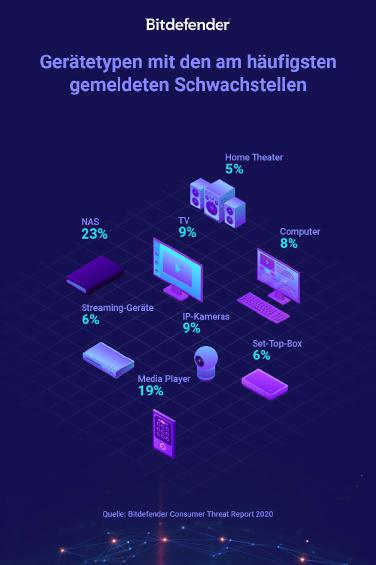
Loopholes in IoT devices, Bitdefender Customer Threat Report 2020 (Image: Bitdefender).
- Perceiving possible dangers: Private users can also be targeted by cyber criminals. They often believe that their own home network is of no interest to attackers. But they are wrong. A luxurious apartment could encourage some hackers to control the digital doorknob. And even if the attackers are not even targeting the user themselves, they still use loopholes in their hardware to start DDoS attacks via their network, for example. Other hackers would like to seize the chance to break into the company network in this way - and maybe even without the user noticing, as they are not attacked immediately.
- Cheap products can cost you dearly: Those who buy for little money are more likely to take a greater risk into their home. As far as safety is concerned, no brands are often poorly equipped. In addition, they often do not have a hotline. If so, it is difficult to reach. A branded device from an established manufacturer usually delivers what it promises and offers better support.
- Update your own IoT equipment: Devices are often used until they no longer work. However, this can be a problem, because many manufacturers only design their products for a short lifespan and not for long-term use. This may also mean that the support has expired if the device is still in use - or even the provider disappears completely from the market.
- Use password hygiene: Users should change the supplied passwords quickly. You should also change them regularly later or use a password manager. Default passwords are not an obstacle for cyber criminals. They have Internet search engines with which they can find IoT devices directly and in large numbers. What information hackers have about a person can be found in services such as https://dehashed.com find out. They offer a quick overview of a possible compromise of your own login data, which is inexpensive and always up to date.
- Keeping an eye on the protection of your own data: IoT devices are made to transfer data. If this data is on a server outside the EU, different and often more lax data protection guidelines will apply to it. One should never forget that.
Manufacturers and users are not solely responsible when it comes to IoT security. Companies would also do well to monitor their employees' access to the corporate network when they are working on the move. If the IT department cannot access the endpoints, protection can also take place at the network level if necessary. Likewise, authorities and industry associations can no longer ignore the need to push ahead with protecting the Internet of Things.
More than PDF at Bitdefender.com
About Kaspersky Kaspersky is an international cybersecurity company founded in 1997. Kaspersky's in-depth threat intelligence and security expertise serve as the basis for innovative security solutions and services to protect companies, critical infrastructures, governments and private users worldwide. The company's comprehensive security portfolio includes leading endpoint protection as well as a range of specialized security solutions and services to defend against complex and evolving cyber threats. Kaspersky technologies protect over 400 million users and 250.000 corporate customers. More information about Kaspersky can be found at www.kaspersky.com/
