External attackers can use various extortion methods to steal sensitive business information. It is therefore also important to consider unknown cyber threats across all attack surfaces. An interesting way: the combination of intrusion detection signatures with network detection response.
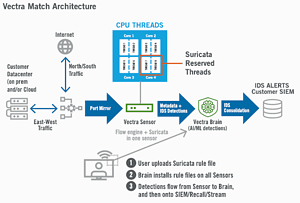
One possible approach is to combine intrusion detection signatures with network detection response. For the IT security provider, these are specifically Vectra Match and Vectra NDR. With the combination of Vectra Match and Vectra NDR, IT teams fighting external threats are able to know how security vulnerabilities are related and how attackers are behaving.
beagle and hunter
Vectra Match takes the context of signatures from intrusion detection, enabling particularly efficient and effective investigation and tracking of attacks. This means that by combining the signature context of Vectra Match and the power of Vectra NDR with Attack Signal Intelligence, you get a complete view of known and unknown threats on your network. SecOps teams can uncover sophisticated attacks across the network, including those that might bypass a traditional intrusion detection system (IDS) or intrusion prevention system (IPS). Vectra Match provides the insights needed to identify and analyze attack situations entering the enterprise from the network edge.
Combination of the advantages of Vectra Match and Vectra NDR
Vectra Match extends the capabilities of Vectra NDR by adding context to intrusion detection signatures, enabling the most efficient and effective threat investigation and hunting. Indeed, in this way, Vectra Match complements Vectra NDR, thereby enhancing the company's entire threat intelligence database: both known and unknown attack situations and vulnerabilities are uncovered.
Vectra Match reinforces the capabilities of Vectra NDR to meet compliance requirements (CRC) and improve security stack operability by forwarding all metadata together to the installed SIEM (Security Information and Event Management). Vectra Match offers the companies a solution that uses existing tools (Vectra NDR) by reducing the expenses for devices (e.g. physical hardware or sensors) when IDS (Intrusion Detection System) with Suricata hardware is required.
When used in conjunction with the Vectra NDR implementation, which leverages Vectra Security's AI-driven Attack Signal Intelligence, Vectra Match provides an automated, risk-based approach to countering cyberattacks:
Do you have a moment?
Take a few minutes for our 2023 user survey and help make B2B-CYBER-SECURITY.de better!You only have to answer 10 questions and you have an immediate chance to win prizes from Kaspersky, ESET and Bitdefender.
Here you go directly to the survey
- Improved Threat Detection and Response: Vectra Match uses the Suricata engine and can therefore detect all known attack signatures, vulnerabilities and malware. This means that Vectra Match can issue an alert for suspicious traffic detected by its own DNS (Domain Name System) resolver, firewall and proxy, in conjunction with leading AI-driven systems. By combining Vectra Match with Vectra NDR, the number of false positives is drastically reduced as all incoming and outgoing traffic is closely monitored and analyzed. This allows infected traffic to be detected when it attempts to enter the network.
- Rich context: By connecting Vectra Match to Vectra NDR, the SecOps team gains the necessary access to signature-based context as well as security-oriented AI and metadata for accurate insights to identify attacks. This provides the security team with appropriate support when hunting down attackers.
- Consolidation of tools: Together, Vectra NDR and Vectra Match along with Suricata provide an AI-driven security solution that enables SecOps teams to uncover more known and unknown attack vectors with a single sensor. With Vectra, your IT teams are able to take timely action to identify points of attack, rather than spending valuable time analyzing and managing disparate security solutions.
About Vectra Vectra is a leading provider of threat detection and response for hybrid and multi-cloud enterprises. The Vectra platform uses AI to quickly detect threats in the public cloud, identity and SaaS applications, and data centers. Only Vectra optimizes AI to recognize attacker methods - the TTPs (Tactics, Techniques and Processes) that underlie all attacks - rather than simply alerting on "different".