
Trend Micro research reveals serious weaknesses in critical IT interfaces for Industry 4.0. Protocol gateways represent a security risk for intelligent industrial environments.
Trend Micro today publishes research showing a new type of vulnerability in protocol gateway devices that could expose Industry 4.0 environments to critical attacks.
These devices, also known as protocol converters, enable machines, sensors, actuators and computers within industrial environments to talk to one another and to connected IT systems.
Protocol gateways can be exploited by attackers as the weakest link in the chain
“Protocol gateways rarely receive individual attention, but they are of great importance for Industry 4.0 environments. They can be exploited by attackers as the weakest link in the chain, ”explains Udo Schneider, IoT Security Evangelist Europe at Trend Micro. "By responsibly disclosing nine zero-day vulnerabilities to affected manufacturers and conducting research for the first time in the industry, Trend Micro is leading the way in making OT environments more secure around the world."
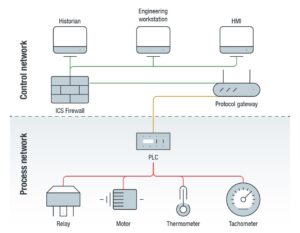
The typical position of a protocol gateway is at the lower end of the control network, directly in front of the process network. (Image source: Trend Micro)
Trend Micro Research analyzed five popular protocol gateways used to translate Modbus, one of the most widely used OT protocols in the world. As detailed in the new report, the following weaknesses and weaknesses can be found in the devices:
- Authentication vulnerabilities that allow unauthorized access
- Weak encryption implementations that allow configuration databases to be decrypted
- Weak implementation of authentication mechanisms that lead to the disclosure of sensitive information
- Enabling denial-of-service attacks
- Errors in the translation function that can be used to issue clandestine commands to disrupt operations
Attacks that exploit such weaknesses can allow malicious hackers to view and steal production configurations and sabotage critical industrial processes by manipulating process control, camouflaging malicious commands with legitimate packages, and denying access to process control.
Expert recommendations
The report contains several key recommendations for manufacturers, integrators and users of industrial protocol gateways:
- Before choosing a gateway, carefully examine its design. Make sure that the device has adequate packet filtering capabilities so that it is not prone to translation errors or denial-of-service attacks!
- Do not rely on a single point of control for the security of the network. Combine ICS firewalls and data traffic monitoring for more security!
- Configure and protect the gateway carefully - use strong credentials, disable unnecessary services and enable encryption, if supported!
- Apply the security management to protocol gateways as well as to any other critical OT system! This includes regular checks for vulnerabilities and misconfiguration as well as regular patches.
The full research report is available directly from Trend Micro.
More on this at Trendmicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.
