In recent years, IT and security teams have faced various developments. Mass adoption of the cloud, increasingly sophisticated attacks, the shift to working from home, and other factors have created a changing environment. As a result, an incident response plan or emergency response plan from a few years ago no longer meets current requirements.
No company wants to be reactive in the event of a security incident. A proactive approach with a solid IR plan helps organizations respond quickly and effectively and resume normal operations as quickly as possible. Many already have an IR plan in place, but no matter how thorough it is, refinements are inevitable. The evolving threat landscape and changing environment require regular changes and improvements.
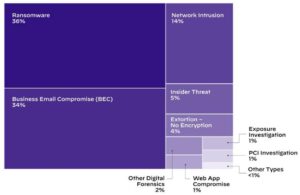
Ransomware and email attacks
Der aktuelle 2022 Unit 42 Incident Response Report for example, has revealed that business email compromise and ransomware attacks are widespread. Together, these two threats account for 70 percent of the cases handled by Palo Alto Networks' Unit 42 research team. While cyber criminals have been engaging in these lucrative activities for years, the specifics continue to evolve. For example, ransomware groups are increasingly using additional extortion mechanisms to get companies to pay. They also create easily accessible versions of their malware to allow less-technical attackers to participate in their malicious activities. By revising existing IR plans, organizations are able to continue defending themselves if attackers change tactics.
Additionally, the top three access vectors for attackers are phishing, exploiting software vulnerabilities, and brute force credential attacks. Therefore, it is important that existing IR plans are revised to focus on the most common types of attacks. Here are seven core best practices that organizations can use to improve their IR plan while strengthening their overall security posture.
Set up regular IR plan communications
When a cybersecurity incident occurs, whether it's a data breach or a ransomware attack, it's important to understand what has been damaged or stolen. Security leaders must stop the attackers and keep the business running normally. However, not knowing where to start can compound the damage. When it comes time to enact or initiate the plan, everyone involved needs to know exactly what to do.
Clear communication and an awareness of the roles and responsibilities of each IR team member is essential to ensure that everyone involved is on the same page. During an incident, everyone needs to be on deck, but for everything to run smoothly, everyone needs to know what the other is doing and who the key contact is for each step of the work. It's also important to see things positively. Responding to security incidents can get hectic, and mistakes are often made. Positive recognition of the team's accomplishments along the way helps keep everyone motivated.
Don't underestimate the value of an IR playbook
Many companies like to say they have an incident response plan in place, but all too often they don't know what to do with it. A threat-specific incident response playbook is essential to an effective IR plan. While this doesn't have to be officially published, it should at least consist of an easily accessible document that can serve as a guide in the chaos of the reaction.
A common problem with cyberattacks and other incidents is that while the groups know what they are responsible for, they do not know how to exercise that responsibility. The playbook should provide guidance on what actions to take to resolve specific situations. It can be thought of as a series of IR SOPs (Standard Operating Procedures).
For example, when containing a ransomware incident, the IR team will likely recognize that passwords need to be changed, but may not be sure to what extent. The playbook would show which passwords need to be changed, ie administrative, individual, service accounts, global accounts, etc. It also includes a checklist of all other required actions and who is responsible for doing them.
Introduce regular safety hygiene reviews
A solid IR plan encourages habits that are conducive to safety. Regular safety hygiene reviews ensure a more efficient response and help minimize the risk of incidents from the outset. These checks include changing passwords, updating and/or rotating keys, checking access levels, and looking for old employee accounts or accounts created by an attacker.
Updating the IR plan as technology changes
Creating an IR plan is not a one-off task, and the plan should be evaluated and reviewed on a regular basis. This is particularly important in today's world where technology and the information systems that support it are rapidly evolving and changing. Other changes can also occur, such as B. the relocation of business processes or changes in personnel and tasks.
As such changes occur, the IR plan must be adjusted to keep up. For example, if organizations have moved some of their data or workloads to the cloud, this exposes them to new threats. As a result, they must adjust their IR plan to address cloud-specific threats.
One thing to note is that companies don't need to reinvent the wheel by designing an entirely new plan. Instead, they should make changes to the existing plan, following the latest best practices, such as: B. the NIST Cybersecurity Framework, CSIRT or BSI (catalog of measures for emergency management).
Proactively evaluate the IR plan
Organizations don't want to wait until it's too late to discover weaknesses in their plan, so a proactive assessment of the IR plan is essential. Also, those responsible for executing the plan will do so much more easily once they have had enough practice. Proactive steps can include IR drills, penetration testing, tabletop drills, and purple teaming. All key stakeholders should be involved in evaluating the plan.
Plan a zero-day budget
Even the best plan can fail if there is no budget for its execution. It's important to budget for the cost of a zero-day incident. A company may have insurance to cover a cyber attack, but it also needs capital to cover additional or unexpected costs. It is also important that the key players know how to use this budget. Leaders don't want to make budget decisions in the middle of an incident or allow the budget to limit their ability to respond appropriately.
For example, in the event of an incident, organizations may need to purchase new computers or other hardware to keep operations running, or invest in software to mitigate an attack. These discussions should be held as early as the IR planning phase so that no uncertainty arises and no time is lost in a tense situation.
Make incident response training a priority
With so much going on in the day-to-day business, it's easy to let incident response training take a backseat. This leads to outdated plans and inadequate responses when it matters most.
All companies, regardless of size, should make IR training a priority. Training should be included in the IR plan and budgeted accordingly. Various scenarios should be discussed and reaction measures practiced so that everyone knows what they are responsible for. In addition, members of the IR team should share their knowledge among themselves to avoid that only one person has specific knowledge of important software, hardware or systems. Formal training should be ongoing as organizations introduce new technologies (such as endpoint, detection, or response tools) into their environment.
"It takes 20 years to build a reputation and a few minutes of a cyber incident to ruin it," said Stephane Nappo, global head of information security at Société Générale International Banking. With so much at stake, it is vital that incident response is fast and effective. Following these best practices for improving the IR plan is key to ensure this.
A solid IR plan that includes preparation, training and testing means that when a security incident occurs, those responsible will be able to rise to the challenge and successfully navigate their organization through the crisis.
More at PaloAltoNetworks.com
About Palo Alto Networks Palo Alto Networks, the global leader in cybersecurity solutions, is shaping the cloud-based future with technologies that transform the way people and businesses work. Our mission is to be the preferred cybersecurity partner and protect our digital way of life. We help you address the world's biggest security challenges with continuous innovation leveraging the latest breakthroughs in artificial intelligence, analytics, automation, and orchestration. By delivering an integrated platform and empowering a growing ecosystem of partners, we are the leaders in protecting tens of thousands of businesses across clouds, networks and mobile devices. Our vision is a world where every day is safer than the one before.