New CrowdStrike Global Threats Report Shows Rise in Ransomware and Disruptive Operations. The report shows that attackers are using “lock-and-leak” operations and cloud service providers are increasingly being targeted by Russia-affiliated cyber actors.
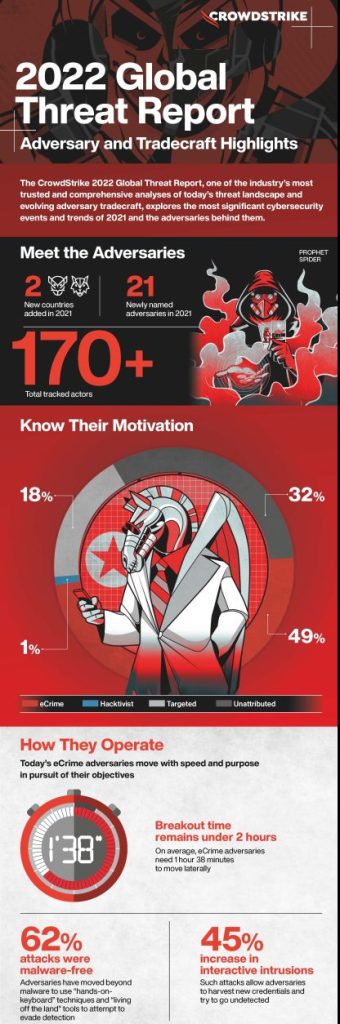
CrowdStrike Holdings, Inc., a leading provider of cloud-based protection for endpoints, workloads, identity and data, announces the release of the 2022 CrowdStrike Global Threat Report. Among other things, the report not only reveals an 82 percent increase in ransomware-related data leaks, but also introduces two completely new groups of nation-state attackers, WOLF (Turkey) and OCELOT (Colombia). In addition, the experts add 21 new groups from around the world to the list of groups watched by CrowdStrike. The 8th annual Global Threat Report also details new operations and techniques from the Big Four: Iran, China, Russia and North Korea. Furthermore, the new report analyzes the consequences of the Log4Shell attacks and shows that attackers are less and less relying on malware, as 62 percent of the most recent discoveries were malware-free.
Ransomware, disruptive operations, cloud-related attacks
The CrowdStrike Intelligence report documents both the continued evolution of state-affiliated and criminal attackers, as well as the increasing sophistication, speed and impact of targeted ransomware attacks, disruptive operations and cloud-related attacks in 2021. Key takeaways from this year's report come from organizations the insights needed to improve their security strategies and protect themselves against numerous cyber threats.
Nation-state and criminal groups continue to expand
The threat landscape in 2021 has expanded with the emergence of new adversaries. CrowdStrike monitors a total of more than 170 such groups today. Notable developments include:
- Financially motivated eCrime activity continues to dominate the interactive intrusion attempts tracked by CrowdStrike OverWatch. Attacks attributable to eCrime accounted for almost half (49%) of all observed activity.
- Iran-based attackers use ransomware and disruptive "lock-and-leak" information operations - they use ransomware to encrypt target networks and then leak information about victims through channels they control.
- In 2021, pro-China players have been at the forefront of exploiting vulnerabilities, increasingly shifting their tactics to internet-enabled devices and services such as Microsoft Exchange. CrowdStrike confirmed the exploitation of 2021 vulnerabilities published in XNUMX by China-affiliated actors.
- Russia-affiliated attacker COZY BEAR extended its attacks on IT to cloud service providers to exploit trusted relationships and gain access to additional targets through lateral movement. In addition, FANCY BEAR has increased its use of credential harvesting tactics, including large-scale scanning techniques and customized phishing websites.
- The Democratic People's Republic of Korea (DPRK) has been targeting cryptocurrency-related businesses to generate illicit revenue during the economic disruptions caused by the COVID-19 pandemic.
- eCrime actors – including DOPPEL SPIDER and WIZARD SPIDER partners – used Log4Shell as an access vector for ransomware operations. Pro-nation state actors, including NEMESIS KITTEN (Iran) and AQUATIC PANDA (China), have also been linked to a likely Log4Shell exploit before the end of 2021.
Attackers' methods are becoming more and more sophisticated
The new GTR report highlights that the immense growth and impact of targeted ransomware attacks, disruptive operations and a surge in cloud-related attacks in 2021 has been felt across almost every industry and country.
- CrowdStrike observed an 82 percent increase in ransomware-related data leaks in 2021, spread across 2.686 attacks as of December 31, 2021, compared to 1.474 attacks in 2020.
- The CrowdStrike eCrime Index (ECX) shows that ransomware attacks were very lucrative throughout 2021. Demonstrating the strength, volume and sophistication of the cybercrime market, the ECX is updated weekly based on 20 unique indicators of criminal activity, tracking things like big game hunting victims, data leaks and ransom demands. Over the course of 2021, the CrowdStrike ECX recorded the following:
- CrowdStrike observed 2.721 cases of big game hunting in the past year.
- CrowdStrike observed over 50 targeted ransomware events per week on average.
- Observed ransomware requests averaged $6,1 million per ransom, up 36 percent from 2020.
- Attackers are increasingly using stolen user information and identities to bypass existing security solutions - of all discoveries indexed in Q2021 62, XNUMX percent were malware-free.
The full CrowdStrike Global Threat Report 2022 can be downloaded online for free.
More at Crowdstrike.com
About CrowdStrike CrowdStrike Inc., a global leader in cybersecurity, is redefining security in the cloud age with its completely redesigned platform for protecting workloads and devices. The lean single-agent architecture of the CrowdStrike Falcon® platform uses cloud-scaled artificial intelligence and ensures protection and transparency across the company. This prevents attacks on end devices both inside and outside the network. With the help of the company's own CrowdStrike Threat Graph®, CrowdStrike Falcon correlates around 1 trillion endpoint-related events worldwide every day and in real time. This makes the CrowdStrike Falcon platform one of the world's most advanced data platforms for cybersecurity.