The Swiss security company Exeon Analytics warns against only relying on conventional EDR solutions (Endpoint Detection & Response) when securing endpoints. Because the agent software does not always run at the end point, which creates weaknesses in the defense network.
Many endpoints in modern, hybrid networks do not support the agents required for this, and where such agents are running, they can be undermined and deactivated by sophisticated attacks. Also, because of the trend towards working from home and BYOD (bring your own device), IT and security teams often don't have access to endpoints owned by employees that may also be used by other family members.
"EDR solutions provide real-time insight into endpoints and detect threats such as malware and ransomware," said Gregor Erismann, CCO of Exeon Analytics. “By continuously monitoring endpoints, security teams can uncover malicious activity, investigate threats, and take appropriate action to protect the organization. However, since EDR only provides visibility into the endpoints, many vulnerabilities and challenges remain, greatly increasing the risk of unnoticed cyberattacks.”
Many endpoints are not supported by EDR
In addition to the possible disabling of EDR agents on the endpoints, these risks also include the abuse of the “hooking” technique that EDR uses to monitor running processes. It enables EDR tools to monitor programs, detect suspicious activity, and collect data for behavioral analysis. However, attackers can use the same technique to access a remote endpoint and import malware.
The endpoints not supported by EDR include older switches and routers in particular, but also a large number of IoT and IIoT devices that can thus become unnoticed gateways for malware. Another problem for EDR solutions can be SCADA environments, where individual critical systems may be outside of the company's control and thus outside the security perimeter of the EDR.
Network Detection and Response as a workaround
"Network Detection and Response (NDR) is a very effective way of closing security gaps like this," says Erismann. “One of the great advantages of log data-based NDR solutions like ExeonTrace is that they cannot be deactivated by attackers and thus the detection algorithms cannot be bypassed. Even if an attacker is able to compromise the EDR system, suspicious activity will still be registered and analyzed. The combination of EDR and NDR creates a comprehensive security system for the entire network.”
In addition, NDR not only enables monitoring of network traffic between known network devices, but also identifies and monitors unknown devices. Such solutions are therefore an effective remedy against the dangers of uncontrolled shadow IT. In addition, NDR also integrates end devices without EDR agents into the network analysis and thus into the company-wide security strategy. Finally, based on the log data analysis, NDR also recognizes incorrectly configured firewalls and gateways, which could otherwise also act as gateways for attackers.
No software agents needed
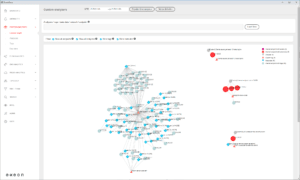
Since NDR solutions like ExeonTrace do not require agents, they allow full visibility of all network connections and data flows. They thus offer a better overview of the entire corporate network and all potential threats within it. In addition, network-based data collection is significantly more tamper-proof than agent-based data, which makes it easier to meet compliance regulations. This applies in particular to the digital forensics required by the supervisory authorities.
NDR with ExeonTrace
The ExeonTrace NDR solution is based on the analysis of network log data and therefore does not require traffic mirroring. ExeonTrace's algorithms have been specially developed for the analysis of metadata and are therefore not affected by the increasing encrypted network traffic. Since ExeonTrace does not require any additional hardware and enables the analysis of multiple data sources including native cloud applications, the solution is particularly suitable for heavily virtualized and distributed networks.
More at Nextgen.Exeon.com
About Exeon
Exeon Analytics AG is a Swiss cybertech company specializing in protecting IT and OT infrastructures through AI-driven security analytics. The Network Detection and Response (NDR) platform ExeonTrace offers companies the opportunity to monitor networks, immediately detect cyber threats and thus effectively protect their own company's IT landscape - quickly, reliably and completely software-based.