Why you should use a qualified time stamp for the e-signature and what secure digital time information with a qualified time stamp guarantee. Finally, Article 41 (2) of the European eIDAS regulation even proves its very high evidential value.
Whether it is about the timely submission of documents, the archiving of patient files, the receipt of offers for large tenders or the protection of signatures based on short-term certificates ("ad hoc") - numerous application scenarios require proof that certain digital data or documents were available in one form and not otherwise at a certain point in time.
A qualified electronic timestamp is the appropriate tool that meets this requirement. It optimally complements the e-signature and reliably proves the original status of documents at a specific point in time.
Very high evidential value according to the eIDAS regulation
Article 41 (2) of the European eIDAS regulation even stipulates the very high evidential value of a qualified time stamp, which is very difficult to shake with counter-evidence. In contrast to this, the local system time of a computer is easy to manipulate and does not have a high evidential value.
Qualified timestamps verifiable for 30 years
Qualified time stamps are not determined by a local computer, but rather generated within a qualified trust service provider and are therefore based on an official, traceable time source. Corresponding providers, such as D-TRUST GmbH (a Bundesdruckerei company), guarantee that the qualified time stamps issued by them can be checked over a period of 30 years.
The time information at D-TRUST is synchronized with the German DCF 77 time signal. In the event of a time signal failure, the deviation is a maximum of 500 milliseconds.
Qualified time stamps to secure "ad hoc" remote signatures
The qualified time stamp plays an important role when using “ad hoc” remote signature certificates (mobile phone signature) that are only valid for a short time. If a person identifies himself / herself for a qualified sign-me remote signature account by video (VideoIdent procedure), a new qualified “ad hoc” signature certificate, valid for 24 hours, is issued for each signature process. In order for the generated qualified signature to be displayed as valid even after the 24 hours have elapsed, a qualified time stamp must be used when signing.
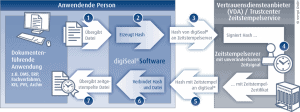
Use time stamps with digiSeal® products
The digiSeal® product range enables the simple integration and use of time stamps in existing processes and applications, such as archive systems (digiSeal®archive) or on the workstation computer (digiSeal®office (pro)). Convenient interfaces such as web service and API are provided for technical integration. The components can also be used stand-alone and out-of-the-box.
With digiSeal®Points (https://shop.secrypt.de/produkt/digiseal-punkte/), qualified D-TRUST time stamps can be created very quickly and easily with the signature software digiSeal®office (https://shop.secrypt.de/ product / digiseal-office /) and billed as needed - even with very small timestamp quantities.
More at secrypt.com
About secrypt
Secrypt GmbH, founded in 2002, specializes in legally compliant electronic signatures, e-seals and time stamps with which digital business processes can be optimized, accelerated and secured. Together with its partners, secrypt offers practice-oriented, flexible and easy-to-integrate solutions. With the digiSeal® product family, secrypt GmbH ensures authenticity, protection against manipulation and confidentiality of sensitive electronic data. The company is a founding member of the CCESigG and contributes its expertise to the relevant specialist committees of BITKOM, TeleTrusT and the Association for Safe Digital Identity.