
According to Radware's security specialists, raids, arrests, and server seizures have no significant impact on the growth of DDoS-as-a-Service: illegal booter and stresser services.
Such services, also known as DDoS-as-a-Service, are offered by many hackers who use this to market their existing botnets when they are not using them for an attack themselves. They act like normal companies according to market economy criteria. The services are now extensively advertised on the Internet search engines instead of on the darknet and social media as they used to be, and fierce competition is causing ever lower prices and thus lowering the entry threshold for amateur hackers.
In the past two years, such illegal offers have come more and more into the focus of the authorities. In late 2018, the FBI seized the domains of 15 Boot Services that were known to be some of the world's leading DDoS-as-a-service offerings. In October 2019, the Dutch police seized servers from the bulletproof hosting provider KV Solutions. These servers were known to be malicious and host several command and control servers for IoT botnets. In April 2020, the Dutch police, who work with hosting services, registrars, international police services, Europol, Interpol and the FBI, seized another 15 unnamed boat services.
Amateurs have taken over the scene
According to Radware, there was a slight decrease in DDoS activity after those responsible were arrested, but these measures were overall ineffective. Because the market for these illegal services has changed. Today it is less the notorious DDoS groups like Lizard Squad who wander around on social media or launch attacks. The darknet forums have largely been abandoned. The landscape appears calm, but it is not. A scene of amateurs has established itself underground who want to impress their friends, cause failures and make a profit.
One of the reasons for the continued growth is the accessibility of open source code, which is used to build IoT botnets. The booter and stresser industry has grown so much, according to Radware, that law enforcement agencies around the world are wondering how to tackle a problem that is spiraling out of control. Google in particular is very popular with providers of booter and stresser services to openly advertise their services. While DDoS is illegal almost everywhere in the world, national laws have not prevented search engine algorithms from indexing criminal websites. Worse still, there is nothing stopping cyber criminals from paying and using search engines to advertise their services.
DDoS-as-a-Service: Advertising via search engines
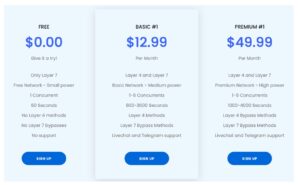
Almost unbelievable: Amateurs even offer DDoS attacks on the Internet as a bookable service for little money.
The basic packages for DDoS-for-hire on the public Internet have remained relatively unchanged over the last 5 years. The basic packages are still between US $ 9,99 and 19,99 per month. Those who pay for the service typically get access to the provider's botnet for 30 days so that they can launch temporary attacks lasting between 300 and 3600 seconds. Up to US $ 5.000 are paid for more powerful packages.
Instagram has also developed into a new platform for the booter and stresser industry. The platform enables bot-herders to advertise their illegal services by posting pictures of their botnets, including the number of their bots. However, here you will mainly find smaller botnets at very low prices that may have disappeared overnight.
Tackle the problem at the root
As history shows, takedowns and arrests are not the long-term solution. Containing the growing booter and stress industry means addressing the core problem, according to Radware: the devices and servers used to create large-scale botnets and record-breaking attack volumes. Radware recommends looking deeper into the growth of the IoT market and the lack of regulation and security standards for devices that connect to the Internet. In addition, the problems associated with open resolvers and reflectors on the Internet need to be addressed. There will always be new attack vectors, but the timely development and, above all, the application of patches could solve many problems. However, the dispersed nature and levels of responsibility for the problems, the lack of financial incentives, and the lack of knowledge and sense of urgency for security create significant challenges.
As long as devices can be infected within seconds and services and resolvers remain open, the problem will persist. According to Radware, the only way to demotivate criminals is to remove the huge attack surface from the bot-herders and at the same time to take appropriate measures to increase the resistance to successful DDoS attacks. The ultimate solution is to make these attacks too difficult and too expensive to carry out. This will put an end to the smaller cyber criminals and would-be hackers.
More on this at Radware.com
About Radware Radware (NASDAQ: RDWR) is a global leader in application delivery and cybersecurity solutions for virtual, cloud and software-defined data centers. The company's award-winning portfolio secures the company-wide IT infrastructure and critical applications and ensures their availability. More than 12.500 enterprise and carrier customers worldwide benefit from Radware solutions to quickly adapt to market developments, maintain business continuity and maximize productivity at low cost.
