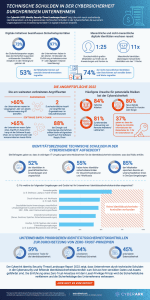
73 percent of the IT decision-makers surveyed in Germany believe that the topic of cyber security and cyber risks has taken a back seat to digital business initiatives in the past year. This is a key finding of a new study by CyberArk.
The new global study "Identity Security Threat Landscape" by security experts CyberArk shows that companies are increasingly using human and machine identities. It often moves on a scale that goes into the hundreds of thousands. This inevitably poses greater cybersecurity risks for businesses.
Evolution of cybersecurity risks
Every comprehensive IT or digital initiative leads to a higher number of interactions between people, applications and processes - and thus to more digital identities. If not adequately managed and unsecured, they can pose a significant cybersecurity risk. The figures from the German companies surveyed prove this danger:
- 74% of non-human identities or bots have access to sensitive data and resources.
- The average employee has access to more than 25 applications and accounts.
- There are now eleven times more machine identities than human identities in a company.
- 85% percent of companies store secrets in multiple places in DevOps environments.
- 71% think developers typically have more permissions than they need to do their jobs.
The attack surface 2022
Trends such as digital transformation, cloud migration and new attack techniques are increasingly jeopardizing IT security. Those responsible for security in Germany see the following cyber threats:
- Circumventing defenses (39%) is the top risk for respondents, followed by accessing credentials (37%) and escalating privileges (37%).
- 69% of the companies surveyed were affected by ransomware attacks in the past year.
- 59% did nothing to secure their software supply chain after the SolarWinds attack, and 66% admit that a software vendor compromise would mean an attack on their organization could not be stopped.
Poor investment in cybersecurity
Security experts agree that enterprise-wide digital initiatives are not adequately supported by security programs and tools. 73% state that their company has prioritized business continuity over ensuring robust cybersecurity over the past 52 months. Additionally, XNUMX% say they have no identity security controls in place for their mission-critical applications.
"Today, companies are exposed to an ever larger attack surface, as the number, types and interconnectedness of identities in business applications, cloud environments and technical components are constantly increasing," explains Michael Kleist, Area Vice President DACH at CyberArk. “Consequently, organizations need to adopt new strategies that put identity security at the core. Our research shows that while the growing security risks are often recognized, the necessary investments in cybersecurity are lacking. There is still an urgent need for action in many companies. Just hoping that you yourself will be spared from a cyber attack should not be an option.”
Possible measures for better defense
What measures can companies take in view of this security situation? Cited by respondents to the CyberArk survey:
- Implementing a strategy to manage sensitive access: The respondents consider three measures to be very important. 55% name the application of least privilege and zero trust principles, 51% the monitoring of SaaS user accounts and access, and 45% the introduction of processes that isolate business-critical applications from the Internet.
- Leveraging Identity Security Controls to Enforce Zero Trust Principles: Solutions for identity security (59%), workload security (54%) and data security (45%) are among the key basic measures for the respondents.
- Increase in transparency: 81% state that a software inventory would reduce the risk of a compromise resulting from the software supply chain.
About the investigation
The 2022 Identity Security Threat Landscape Report highlights the findings of research conducted by market research firm Vanson Bourne on behalf of CyberArk. 1.750 IT security decision-makers in Germany, France, Great Britain, Italy, Spain, Australia, Brazil, Mexico, Israel, Japan, Singapore and the USA were surveyed.
More at CyberArk.com
About CyberArk CyberArk is the global leader in identity security. With Privileged Access Management as a core component, CyberArk provides comprehensive security for any identity - human or non-human - across business applications, distributed work environments, hybrid cloud workloads and DevOps lifecycles. The world's leading companies rely on CyberArk to secure their most critical data, infrastructure and applications. Around a third of the DAX 30 and 20 of the Euro Stoxx 50 companies use CyberArk's solutions.