
Cybercrime 2021: Ransomware continues to be the top dog. In the current Sophos Threat Report 2021, the Sophos experts give their assessments of the upcoming IT security trends from different perspectives.
Sophos presents its latest Sophos Threat Report 2021. It shows that ransomware, especially with the phenomenon of secondary extortion and the rapidly changing behavior of cyber criminals, will have a decisive impact on the threat landscape and IT security in the coming year. The Sophos Threat Report was written by SophosLabs, Threat Hunters, the Rapid Respons team, as well as cloud and AI experts, and provides both a comprehensive overview of the security threats of the past year and an outlook on the expected threats in the coming year.
Three important security trends for 2021
1. The gap between skills and resources of the various ransomware actors continues to grow. Savvy ransomware criminals are continually refining and changing their tactics, techniques, and procedures to target larger organizations and businesses with millions in ransom demands. In 2020, this ransomware category included Ryuk and RagnarLocker, for example. In addition, the Sophos experts expect an increasing number of ransomware newcomers. These mostly work with menu-driven rental ransomware like Dharma, with which they can attack many targets with small ransom demands.
Another ransomware trend for 2021 is what is known as “secondary blackmail”. In addition to data encryption, the attackers also steal sensitive or confidential information and threaten to publish it if the requirements are not met. Popular examples of this approach are the Maze, RagnerLocker, Netwalker, and REvil ransomware families.
Popular families of ransomware
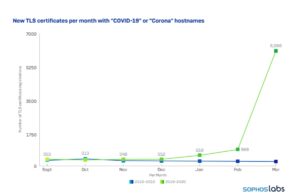
TLS certificate registrations related to the pandemic rose around the same time as domain registrations (source: SophosLabs).
“The ransomware business model is dynamic and complex. In 2020, we saw a clear trend at Sophos that attackers differ in their skills and goals. It was also noticeable that “best-of-breed” tools were and are used again and again by certain ransomware families, ”says Chester Wisniewski, Principal Research Scientist at Sophos. “Some ransomware families like Maze seemed to be disappearing, but the tools and techniques used in these attacks reappeared under the guise of a new ransomware like Egregor. The disappearance of well-known players in the ransomware market is not a sign of the all-clear, because when one threat disappears, another quickly takes its place. In many ways, it is almost impossible to predict what ransomware attacks will look like in the future. But the attack trends discussed in the Sophos Threat Report in early 2020 are expected to continue into 2021. "
2. Everyday threats like malware including loader programs and botnets or opportunistic hackers who deal with access data continue to represent a major challenge for IT security teams. Such attacks are designed in such a way that they collect important data from their target and pass it on to a command-and-control- Submit network. There, the intruders check each compromised device for geolocation and other valuable information and sell this information to the highest bidder, such as a large ransomware group. For example, this year Ryuk used the Buer Loader to deliver ransomware to the victims.
Any infection can infect an entire system
“Everyday malware in particular should not be dismissed as 'background noise', as these attacks can literally clog the security warning system with many individual attacks. It is clear from our analyzes that these attacks must also be taken very seriously, as every single infection can infect an entire system. As soon as malware is blocked or removed and the compromised computer has been cleaned, many people close the chapter for the last time, ”says Wisniewski. “However, many may not be aware that the attack was probably directed against more than just one computer and that apparently simply blocked malware such as Emotet or Buer Loader can subsequently open the door to more advanced attacks with, for example, Ryuk or Netwalker. IT departments often only notice this when the ransomware is used. So underestimating these 'minor' infections can prove very costly. "
3. Cyber criminals are increasingly abusing legitimate tools, well-known utilities, and widely used network targets to evade security measures. The misuse of commonly used standard programs allows cyber criminals to stay under the radar of the network until they launch the attack. State-motivated attackers also have the advantage that the use of neutral programs makes the assignment more difficult in the event of detection. In 2020, Sophos reported on the wide range of such standard attack tools.
Rapidly growing threat hunting area
“Misusing everyday tools and techniques to obfuscate an attack challenges traditional security approaches because the use of such programs does not automatically trigger an alert. This is where the rapidly growing area of threat hunting comes into its own thanks to a team of experts and the controlled response to threats, ”says Wisniewski. “These experts know the subtle anomalies and traces of an attack to look for. This includes, for example, a legitimate tool that is used at the wrong time or in the wrong place. For trained threat hunters or IT managers who use Endpoint Detection and Response (EDR) functions, these signs are valuable pointers to warn of a potential intruder and an ongoing attack. "
The other trends from the Sophos Threat Report 2021
- Attacks on servers: Cyber criminals target server platforms under Windows and Linux and use these platforms to attack organizations from within.
- The COVID-19 pandemic has an impact on IT security. This includes, for example, securing the home office with personal networks based on very different security levels.
- Security challenge in cloud environments. With cloud computing, however, companies face different challenges than with a traditional corporate network.
- Standard services such as RDP and VPN are still the focus of the attackers. RDP is also used to expand further within the networks.
- Applications traditionally marked as “Potentially Unwanted” (PUA) because they deliver a wealth of advertisements. These use tactics that are increasingly indistinguishable from overt malware.
- The surprising reappearance of an old bug: VelvetSweatshop is a standard password feature for earlier versions of Microsoft Excel that was used to hide malicious macros or other critical content in documents in order to evade threat detection.
- The need to apply epidemiological approaches. These help quantify undiscovered and unknown cyber threats in order to close detection gaps, better assess risks and define priorities.
Straight to the thread report at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.
