
Varonis security researchers have discovered a way to bypass multi-factor authentication (MFA) via SMS for Box accounts. Attackers with stolen credentials were able to compromise an organization's Box account and exfiltrate sensitive data without having to access the victim's phone.
Security researchers reported this vulnerability to Box on November 3, 2021 via HackerOne, which prompted it to be closed. Just last month, Varonis Thread Labs demonstrated how to bypass Box's TOTP-based MFA. Both gaps make it clear that cloud security should never be taken for granted, even when using apparently secure technologies, and that a multi-layered security strategy is required.
SMS code without victim's phone
Like most applications, Box allows users without single sign-on (SSO) to use an authenticator app (like Okta Verify or Google Authenticator) or an SMS with a one-time security code as the second step of authentication. After entering a username and password in the login form, Box sets a session cookie and directs the user to either a form to enter a temporary one-time password (TOTP) if the user is logged into an authenticator app, or a form to enter one SMS codes if the user has opted in to receive a security code via SMS.
Dangerous mixing of MFA methods
A session cookie is also generated if the user does not navigate to the SMS verification form. Similarly, attackers only need to enter the user's email address and password, which they have already phished or purchased on the dark web, to receive a valid session cookie. After the cookie is generated, the attackers can cancel the SMS-based MFA mechanism (where the user is signed in) and instead initiate the TOTP-based MFA mechanism, thus mixing the MFA modes.
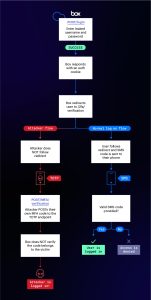
Flow of the Box Attack
- In multi-factor authentication, the attacker logs in with an authenticator app and saves the device's factor ID.
- The attacker enters the victim's email address and password at account.box.com/login.
- If the password is correct, the attacker's browser receives a new authentication cookie and is redirected to /2fa/verification.
- However, the attacker does not follow the redirect to the SMS verification form, instead posting their own factor ID and code from the authenticator app to the TOTP verification endpoint /mfa/verification.
- The attacker is now logged into the victim's account, who doesn't receive an SMS message and thus doesn't notice anything
The course of such an attack is illustrated in this YouTube video.
Findings from the attack
MFA is an important step towards a safer internet and more reliable authentication for SaaS applications. That said, MFA can provide a false sense of security: just because MFA is enabled doesn't necessarily mean that an attacker needs to gain physical access to a victim's device in order to compromise their account. Therefore, reliable authentication can only ever be one level of security.
Accordingly, this vulnerability also illustrates the need for a data-centric approach. "Relying solely on perimeter protection and strong authentication is grossly negligent," explains Michael Scheffler, Country Manager DACH at Varonis Systems. “Security leaders should ask themselves the following questions to review the effectiveness of their security strategy and make adjustments where necessary: Can I tell if MFA has been disabled or bypassed for a user across all of my SaaS applications? How much data can an attacker access if they compromise a regular user account? Do users only get access to files they actually need? And are we able to detect when a user is accessing data in unusual ways?”
More at Varonis.com
About Varonis Since its founding in 2005, Varonis has taken a different approach than most IT security providers by placing company data stored both locally and in the cloud at the center of its security strategy: sensitive files and e-mails, confidential customer, patient and Employee data, financial data, strategy and product plans and other intellectual property. The Varonis data security platform (DSP) detects insider threats and cyber attacks through the analysis of data, account activities, telemetry and user behavior, prevents or limits data security breaches by locking sensitive, regulated and outdated data and maintains a secure state of the systems through efficient automation .,
