Bitdefender Labs uncover military cyber espionage: The Naikon hacker group uses side-loading techniques and powerful backdoors for espionage and data exfiltration.
During an analysis of the misuse of vulnerable legitimate software, Bitdefender Labs uncovered long-running cyber espionage by the well-known APT group Naikon. Naikon has been active for more than a decade. The Chinese-speaking group focuses on high-level targets such as government agencies and military organizations. The evidence gathered suggests that the campaign aimed at espionage and data exfiltration. Such attacks, which follow the example in one of the most cyber-dangerous regions currently - Southeast Asia - are also conceivable in Europe.
Military organizations in Southeast Asia targeted
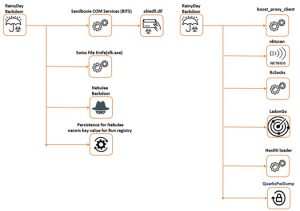
Bitdefender Labs experts found that the victims of this operation are military organizations in Southeast Asia. The campaign was active between June 2019 and March 2021. At the beginning of the operation, the attackers used the Aria body loader and a new backdoor called “Nebulae” as the first stage of the attack. From September 2020, the group added the RainyDay backdoor to its toolkit.
Sideloading techniques are used
DLL hijacking and other sideloading techniques have been around for a long time. They occur frequently and can be fended off well in theory. But what looks simple on paper quickly becomes a problem in the increasingly complex software world. That is why hackers use sideloading to compromise - both for private and government clients. As part of this wave of attacks, the Naikon group also abused numerous legitimate applications.
New backdoor / kill chain reconstructed
Bitdefender Labs also discovered a new backdoor, which they named "Nebulae". Nebulae acts as a backup for intruders as soon as the defense has removed the primary backdoor. The Bitdefender experts were able to reconstruct the complete kill chain of this Naikon Group's campaign and list all the tools used. Bitdefender presents all the details of the attack in an English-language PDF report.
More at Bitdefender.com