Zero Trust is the answer to modern cybercrime, and Sophos is putting that belief into action by incorporating its Zero Trust Network Access (ZTNA) solution into its Intercept X endpoint solution. This further simplifies and improves protection against ransomware and future threats on the cyber floor. An interview with Michael Veit, security expert at Sophos.
In their history, cybersecurity products have primarily focused on preventing malicious code from entering and executing computers. Currently, however, a trend can be observed that requires a rethink: the growing certainty that prevention is not perfect, the detection of malicious attempts to intrude networks is moving to the fore.
Zero Trust Network Access—ZTNA
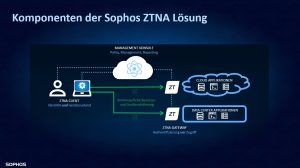
In this context, Sophos is responding with a new solution that integrates seamlessly into the Adaptive Cybersecurity Ecosystem: the Zero Trust Network Access module, which can be fully integrated into the Intercept X endpoint solution and thus a transparent and scalable security model represents. The ability to integrate ZTNA into Intercept X, including XDR (Extended Detection and Response) and MTR (Managed Threat Response), removes much of the complexity associated with managing multiple vendors and agents and provides end-to-end protection for endpoints , users and their identities as well as applications and networks. Zero Trust or Zero Trust Network Access is one of Sophos' most important strategies for the whole of 2022 and beyond.
Where VPN fails, it's time for ZTNA
B2B Cyber Security: Is VPN now obsolete?
Michael Veit, Sophos: “Many traditional remote access solutions such as remote desktop, IPsec or SSL VPN offer strong encryption, but otherwise little protection against modern threats. We see attackers increasingly exploiting these limitations by injecting login credentials into RDPs and VPNs to gain network access. Once in, they roam freely, all too often resulting in costly data theft and ransomware incidents. People, applications, devices and data are no longer confined to the office space – they are everywhere and we need more ways to protect them. Zero Trust is a very effective security principle and Sophos ZTNA embodies this in a viable and easy-to-use solution to ensure users have secure access to the resources they need.”
B2B Cyber Security: Is ZTNA Better Than VPN?
Michael Veit, Sophos: The ZTNA micro-segments network to protect against attacks, stealthy network activity and data theft. The module permanently authenticates user identities with multiple factors, validates the state of the devices, offers stricter user access controls and thus fewer points of attack for cybercriminals. Unlike VPNs, which provide broad network access, ZTNA eliminates this tacit trust and only grants the user access to specific applications and systems on the network. “Trust nobody, verify everything” – with this belief, ZTNA improves protection, simplifies administration for IT managers and offers employees a hassle-free working experience wherever they work.
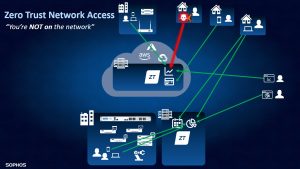
With ZTNA, employees access web applications with their data via the cloud and not directly on the company network (Image: Sophos).
B2B Cyber Security: Will ZTNA make access more secure?
Michael Veit, Sophos: ZTNA helps companies protect themselves from classic attacks through stolen access data or hacked access that lead directly into the network. If an external employee wants to access his work data, he used to have to dial into the network and act as if he were at his desk. But access to the network could fall into the hands of attackers. This is more secure with ZTNA: If the external employee has to access his data, he only gets access to a web application that makes his data available for use. Only the application accesses the network, but not the user. This eliminates a lot of attack surface and the employee can work without hurdles.
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.