Current banking Trojan campaign hides attack methods behind new supposed content. Bitdefender experts are investigating the new variants of the banking Trojans FluBot and TeaBot, which target smartphones in Germany.
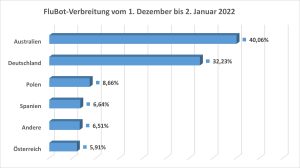
Bitdefender Labs experts have been monitoring new variants of the FluBot and TeaBot banking Trojans since December 2021. Over 100.000 malicious SMS were registered in Bitdefender telemetry alone during this period. An important focus of the attacks in December 2021 was Germany with 32,23%. Only Australia was hit harder. The criminal actors have now adapted their campaigns and are now luring people with supposedly new content. At the same time, they are shifting the focus of shipping between different countries and time zones. The main focus of the recent attacks are European countries.
Proven functionalities with phishing
The banking Trojans such as FluBot, TeaBot or the fraudulent SMS with the enticing subject "Is that you in the video?" are examples of long-term phishing campaigns that the criminal operators periodically play out again and again. The goal is always the same: It is about reading information about online banking, SMS, contact or other private data from infected devices.
The malware types offer an arsenal of commands for this purpose. Thanks to them, the hackers easily arrange for a command-and-control server to send various types of content as SMS. The dropper's host domains remain the same. This allows cyber criminals to attack customers from different banks one after the other and adapt content and functionalities.
FluBot Bait: SMS, Messenger, Phishing
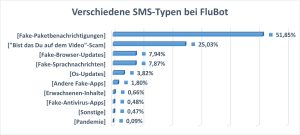
The main content of the malicious SMS, which the authors spread with the FluBot malware, are supposed messages from parcel services (51,85%), followed by a subject with the question: "Is that you on the video?" (25,03% ) (see Figure 1). This well-known phishing, previously carried out via Facebook Messenger, has now become part of a FluBot phishing campaign. The victims first receive an SMS with the subject. In order to be able to see the video afterwards, they are prompted to install a supposed flash or operating system update and then receive the banking Trojan.
Fake browser updates, voice messages, and operating system updates are less common. Fake apps (even fake antivirus apps) or even adult content are less likely to be a hook for FluBot. Striking: Corona content currently plays no role with only 0,09%.
Changing shipping areas
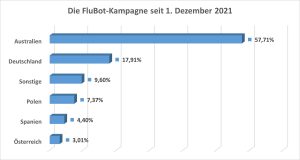
The FluBot operators change their target areas in a very short time - often after just a few days. In addition to Australia, the campaign was also active in Germany (second place with 2%), Spain, Italy and other European countries in December.
Since January, the focus has increasingly shifted to Poland, the Netherlands and Romania. Overall, despite the decline, Germany has remained in second place in the distribution areas over the past two months with a share of 17,91%.
TeaBot distributes fake apps and QR codes - also via Google Ads
Using its telemetry data, Bitdefender Labs observed how a new malicious "QR Code Reader scanner app" was downloaded over 100.000 times in 17 month in XNUMX different variants via Google Play. This is most likely a highly encrypted TeaBot dropper. The TeaBot attack is characterized by offering supposedly useful apps in the Google Play Store. Alternatively, it disguises itself as a fake version of popular apps and then installs the malware as a dropper when downloaded. The QR scanner app is spreading mostly in the UK, and even via Google Ads as well.
More at Bitdefender.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de