Proofpoint's security experts have uncovered a new cyber campaign that is particularly targeting NATO allies. The TA473 hacker group, an Advanced Persistent Threat (APT) actor, is using an IT vulnerability called "Zimbra vulnerability" (CVE-2022-27926) for its current campaign.
The target of their attacks are publicly accessible webmail portals hosted by Zimbra (the Zimbra Collaboration Suite is an e-mail and groupware solution). As part of their activities, the attackers attempt to gain access to e-mails related to the war between Russia and Ukraine from military, governmental and diplomatic organizations in Europe. The APT group TA473 is also known as Winter Vivern or UAC-0114.
Strong attacks on western targets
The group uses scanning tools such as Acunetix to identify unpatched webmail portals owned by relevant organizations and find ways to gain access. After the initial scans, the attackers send phishing emails that impersonate trusted government agencies and link to malicious URLs in the email body. These URLs are designed to exploit known vulnerabilities to run JavaScript on the target organization's webmail portals.
In addition, attackers seem to spend a lot of time examining their victims' individual webmail portals and writing custom JavaScript payloads to perform cross-site request forgery (CSRF) attacks. These labor-intensive, custom-tailored payloads allow attackers to steal usernames and passwords, as well as store active session and CSRF tokens in cookies that facilitate logging into publicly-facing NATO organization webmail portals.
APT group TA473 active for years
“We have been following TA473's activities for about two years. The group is characterized by tenacity and high commitment,” comments Michael Raggi, security researcher at Proofpoint. “This group has persistently targeted American and European officials, as well as military and diplomatic personnel in Europe. Since the end of 2022, TA473 has spent a lot of time studying the webmail portals of European government agencies and scanning the publicly accessible infrastructure for vulnerabilities. Ultimately, they want to gain access to the emails of those in government circles connected to Russia's war against Ukraine.”
This is how the attacks of TA473 work
The following phishing tactics have been observed on both US and European targets, as well as credential stealing, malware distribution, and cross-site request forgery campaigns.
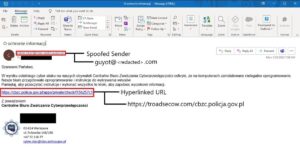
- TA473 sends emails from compromised email addresses. Often these emails come from WordPress-hosted domains that are unpatched or insecure at the time of the compromise.
- TA473 spoofs the sender field of the email to impersonate the user of the target organization.
Or TA473 forges the sender field of the email to pose as an organization commonly known in world politics.
- TA473 uses a non-suspicious URL of either the target organization or a relevant partner organization in the body of the email.
- TA473 then links this harmless URL to infrastructure it controls or compromises to deliver a first-stage payload or redirect to a landing page used to collect credentials.
- TA473 often uses structured URL paths that include a hash value for the target, an unencrypted reference to the target organization, and in some cases encrypted or plaintext versions of the non-suspicious URL linked to the target in the original email.
About Proofpoint Proofpoint, Inc. is a leading cybersecurity company. The focus for Proofpoint is the protection of employees. Because these mean the greatest capital for a company, but also the greatest risk. With an integrated suite of cloud-based cybersecurity solutions, Proofpoint helps organizations around the world stop targeted threats, protect their data, and educate enterprise IT users about the risks of cyberattacks.