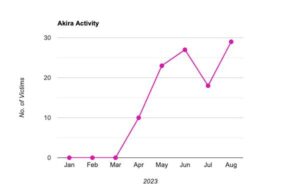
The Akira ransomware group quickly gained notoriety. The group emerged in March 2023 and was already the fourth most active group in August, demanding millions of dollars in ransom from its victims. Logpoint analyzed the tactics, techniques and processes.
Akira primarily focuses on companies across a range of sectors in the UK and US, including education, finance, real estate, manufacturing and consulting.
“Akira has proven to be extremely active and has amassed an extensive list of victims in a short period of time. With each attack, the group evolves with additional capabilities,” says Swachchhanda Shrawan Poudel, Logpoint Security Research Engineer. “The group has already had a number of victims since its emergence in March and there is no sign that its activities are decreasing. The opposite is true, as the number of victims increases every month.”
APT Akira already at number 4 in the rankings
The ransomware is a sophisticated malware that aims to encrypt the files on a victim's system, delete shadow copies, and provide instructions for paying the ransom and data recovery. It uses encryption algorithms, exclusion criteria and a communication system based on TOR to carry out malicious operations.
Logpoint's investigations uncovered Akira's infection chain through malware analysis. Akira is actively targeting Cisco ASA VPNs without multifactor authentication to exploit CVE-2023-20269 as an entry point for their ransomware. The group's members use various malware patterns in their attacks that trigger a series of steps to encrypt victim files, including deleting shadow copies, searching for files and directories, and the process of enumeration and encryption.
Akira ransomware acts mercilessly
“The emergence of Akira shows how important basic cybersecurity measures are,” says Swachchhanda Shrawan Poudel. “In this case, implementing multi-factor authentication can mean the difference between a devastating cyberattack and a harmless attempted attack. Companies must monitor risks and take appropriate protective measures. This includes updating software and systems, checking privileged accounts and segmenting the network.”
Logpoint's security operations platform, Converged SIEM, provides comprehensive tools and capabilities to identify, assess and mitigate the impact of Akira ransomware. With features like native endpoint solution AgentX and SOAR with preconfigured playbooks, security teams can automate key incident response steps, collect critical logs and data, and accelerate malware detection and remediation.
Logpoint has a full report on Akira on its blog. There you get a deep insight into the infection chain, the technical analysis of malware samples and recommendations for protection against the threat.
More at Logpoint.com
About Logpoint
Logpoint is the manufacturer of a reliable, innovative platform for cybersecurity operations. With the combination of advanced technology and a deep understanding of customers' challenges, Logpoint strengthens the capabilities of security teams and helps them combat current and future threats. Logpoint offers SIEM, UEBA, SOAR and SAP security technologies that converge into a complete platform that efficiently detects threats, minimizes false positives, autonomously prioritizes risks, responds to incidents and more.