Cybereason Uncovers Global Chinese Cyberespionage Campaign Targeting North American, European and Asian Companies “Operation CuckooBees” unveils the elusive Winnti Group (APT 41), which has been operating undetected since 2019 against defense, energy, aerospace, Biotech and Pharma operates.
Cybereason, the XDR company, releases new research on Operation CuckooBees. The 41-month investigation into the global cyber espionage campaign shows that the Winnti Group (APT XNUMX) is targeting industrial companies in North America, Europe and Asia. Target groups are companies from the fields of defence, energy, aerospace, biotechnology and pharmaceuticals.
12-month investigation: Operation CuckooBees
Cybereason's investigation found that Winnti had been running Operation CuckooBees unnoticed since at least 2019, likely stealing thousands of gigabytes of intellectual property and sensitive proprietary data from dozens of companies in the process. Cybereason publishes two reports, the first examining the tactics and techniques used throughout the offensive, while the second provides a detailed analysis of the malware and exploits used.
“The results of Operation Cuckoo Bees are the culmination of a 41-month investigation that reveals the complicated and extensive actions of the Chinese state-backed Winnti Group (APT 2019). The group aims to steal proprietary information from dozens of global defense, energy, biotech, aerospace and pharmaceutical companies. Particularly alarming is the fact that the affected companies were unaware that they were being attacked - going back at least as far as XNUMX in some cases. This gave Winnti free and unfiltered access to intellectual property, blueprints, sensitive diagrams and other proprietary data,” said Lior Div, CEO and co-founder of Cybereason.
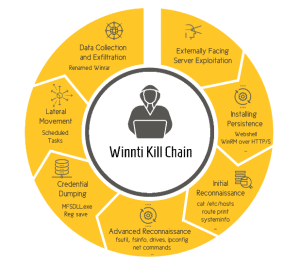
Operation CuckooBees - the most important results
- Assignment to the Winnti APT group: Based on the analysis of the forensic artifacts, Cybereason has a medium to high certainty that the perpetrators of the attack are connected to the notorious Winnti group. This group has existed since at least 2010. It is believed to be operating on behalf of China and specializes in cyberespionage and intellectual property theft.
- Years of cyber espionage operations: Cybereason's IR team investigated a sophisticated and elusive cyberespionage campaign that had gone undetected since at least 2019. Their goal was to steal sensitive proprietary information from technology and manufacturing companies mainly in East Asia, Western Europe and North America.
- Newly discovered malware and multi-stage chain of infection: The investigation reveals both known and previously undocumented Winnti malware, which includes digitally signed kernel-level rootkits and a sophisticated multi-stage infection chain. This has allowed the attack to go undetected since at least 2019.
- The Winnti Playbook: Cybereason offers a unique look at the playbook used by Winnti for intrusion. It describes the most commonly used tactics, as well as some lesser-known evasion techniques observed during the investigation.
- Discovery of a new malware in the Winnti arsenal: The reports reveal a previously undocumented malware strain called DEPLOYLOG used by the Winnti APT group. They also introduce new versions of well-known Winnti malware, including Spyder Loader, PRIVATELOG, and WINNKIT.
- Rarely seen abuse of the Windows CLFS feature: The attackers used the Windows CLFS mechanism and NTFS transaction manipulation to hide their payloads and evade detection by traditional security products.
- Complicated and interdependent delivery of payloads: The reports include an analysis of the complex infection chain leading to the proliferation of the WINNKIT rootkit, which consists of several interdependent components. The attackers took a delicate “house of cards” approach, in which each component depends on the others for proper execution. This makes it very difficult to analyze each component individually.
“The security vulnerabilities most common in attacks like Operation Cuckoo Bees are unpatched systems, poor network segmentation, unmanaged assets, forgotten accounts, and failure to deploy multi-factor authentication products. Even if these vulnerabilities sound trivial and easy to fix, day-to-day security is complex and it is not always easy to find large-scale remedies. Defenders should align with MITER and/or similar frameworks to ensure they have the right vulnerability detection and remediation capabilities to protect their most critical assets,” adds Div.
More at cybereason.com
About Cybereason Cybereason offers future-proof protection against attacks by means of a uniform security approach, across all endpoints and across the company, wherever the attack scenarios are relocated. The Cybereason Defense Platform combines the industry's best detection and response methods (EDR and XDR), next generation antivirus solutions (NGAV) and proactive threat hunting to provide contextual analysis of every element within a Malop ™ (malicious operation). Cybereason is a privately held international company headquartered in Boston with customers in over 45 countries.