Team1's State of XIoT Security Report: 2022H 82 shows an increase in IoT vulnerabilities, vendor self-identified vulnerabilities, and fully or partially fixed firmware vulnerabilities. On average, 125 XIoT vulnerabilities are published and fixed per month.
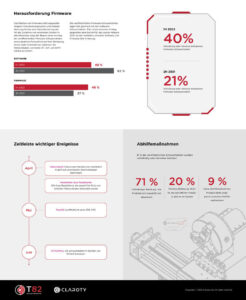
Disclosures of vulnerabilities in IoT devices increased by 2022 percent in the first half of 57 compared to the previous six months. This is shown by the new State of XIoT Security Report: 1H 2022 from Claroty, the specialist for the security of cyber-physical systems (CPS). In the same period, the security gaps disclosed by manufacturers themselves have increased by 69 percent and have thus exceeded the number of reports from independent security researchers for the first time. Fully or partially patched firmware vulnerabilities have increased by 79 percent, a notable improvement given the challenges of patching firmware versus software vulnerabilities.
OT and ICS areas are also affected
Prepared by Claroty's award-winning research team, Team82, the report provides a comprehensive analysis of published vulnerabilities in the enhanced Internet of Things (XIoT), the network of cyber-physical systems that powers operational technology (OT) and industrial control systems (ICS), the Internet of Medical Things (IoMT), building management systems and enterprise IoT. The report includes vulnerabilities discovered by Team82 as well as those that come from trusted open sources. These include the National Vulnerability Database (NVD), the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), CERT@VDE, MITER and the industrial automation providers Schneider Electric and Siemens.
Other key results
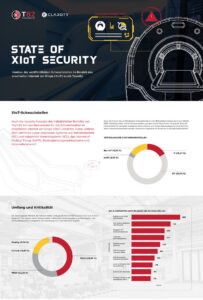
- IoT devices: 15 percent of the vulnerabilities were found in IoT devices. This is a significant increase from 9 percent in Team82's last report for the second half of 2021. Additionally, the combination of IoT and IoMT vulnerabilities (18,2%) outperformed IT vulnerabilities (16,5%) for the first time . This illustrates the increased awareness among manufacturers and security researchers of the security of these connected devices, which can serve as gateways into the networks.
- Vulnerabilities disclosed by manufacturers themselves: For the first time, disclosures from manufacturers (29%) have surpassed reports from independent researchers (19%), ranking second behind security companies (45%). With 214 published CVEs, the number of reported vulnerabilities has almost doubled compared to the last half year (127). This indicates that more OT, IoT and IoMT vendors are setting up vulnerability disclosure programs and devoting more resources to testing the security of their products than ever before.
- Firmware: Published firmware vulnerabilities were almost par with software vulnerabilities (46% and 48%, respectively). This is a huge increase from the report for the second half of 2021, when the ratio between software (62%) and firmware (37%) was almost 2:1. The report also shows a significant increase in fully or partially fixed firmware vulnerabilities (40% in H2022 21 vs. 2021% in HXNUMX XNUMX), which is notable given the challenges of patching firmware due to longer update cycles and infrequent maintenance windows. This is likely due to a growing interest among researchers in securing devices at the lower levels of the Purdue model, which are more directly connected to the actual process and thus represent a more attractive target for attackers.
- Scope and criticality: On average, 125 XIoT vulnerabilities are published and fixed per month, for a total of 2022 vulnerabilities disclosed in the first half of 747. The vast majority are classified as high (46%) or critical (19%) according to their CVSS score.
- Effects: Almost three quarters (71%) of vulnerabilities have a high impact on system and device availability. The most common potential impact is unauthorized remote code or command execution (accounting for 54% of vulnerabilities), followed by denial of service conditions (crash, exit, or reboot) at 43%.
- Remedial Actions: The most common remediation measure is network segmentation (recommended for 45% of vulnerability reports), followed by secure remote access (38%) and protection against ransomware, phishing and spam (15%).
- Team82: Team82 continues to be at the forefront of OT vulnerability research, uncovering 2022 vulnerabilities in the first half of 44 for a total of 335 vulnerabilities to date.
The full findings, in-depth analysis, and additional measures to protect against unauthorized access and risks can be found in Claroty's semi-annual State of XIoT Security Report: 1H 2022.
More at Claroty.com
About Claroty Claroty, the Industrial Cybersecurity Company, helps its global customers discover, protect and manage their OT, IoT and IIoT assets. The company's comprehensive platform can be seamlessly integrated into customers' existing infrastructure and processes and offers a wide range of industrial cybersecurity controls for transparency, threat detection, risk and vulnerability management and secure remote access - with significantly reduced total cost of ownership.