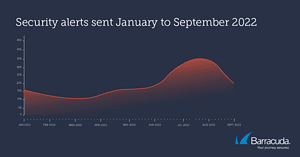
As a Barracuda analysis shows, the severity of security threats increases during the holiday season from cyber attackers. One in five cyber threats between June and September 2022 presented an increased risk, compared to just one in 80 in January of the year.
The latest threat intelligence, coming from Barracuda's XDR platform and 24/7 Security Operations Center, shows how threat severity has evolved in 2022. In January 2022, only about 1,25 percent of threat alerts were serious enough to warrant a security alert to the customer.
June to September more potential dangers
However, of the alerts analyzed by Barracuda threat researchers between June and September, 20 percent were severe enough to alert the customer to the potential threat and prompt them to take corrective action.
The three most detected threats between June and September:
1. Successful sign-in to Microsoft 365 from a suspicious country - "high risk"
These types of attacks accounted for 40 percent of all threats analyzed between June and September. Countries that trigger an automatic security alert include Russia, China, Iran and Nigeria. "High risk" threats are events that have the potential to cause severe damage to the customer environment and require immediate action. A successful intrusion into a Microsoft 365 account is particularly risky as it gives an attacker potential access to any networked and integrated resources that the attack target has stored on the platform.
2. Communication to an IP address known to threat intelligence - "medium risk"
This type of attack, which accounted for 15 percent of all attacks, involves any attempt at malicious communication from a device on the network to a website or a known command and control server and similar. A "moderate risk" requires remedial action, but as a single event does not usually result in a significant impact.
3. User brute force authentication attempt – “medium risk”
These automated attacks, which accounted for 10 percent of all attacks, attempt to penetrate an organization's defenses simply by trying as many name/password combinations as possible.
Cyber attackers target companies and IT security teams when resources may not be available, such as on weekends, overnight, or during holiday periods. The analysis results above show that companies should plan for this in their security strategy for upcoming holiday seasons.
To counter this risk, companies should take the following security measures
- Enable multi-factor authentication (MFA) for all applications and systems.
- Ensuring that all critical systems are backed up.
- Implementing a robust security solution that includes email protection and endpoint detection and response (EDR).
- Visibility across the entire IT infrastructure.
- A XNUMX/XNUMX Security Operations Center (SOC) to monitor, detect and respond to cyber threats, either in-house or through a trusted service provider.
More at BarracudaMSP.com
About Barracuda MSP To thrive in today's ever-evolving cyber threat landscape, managed service providers must run their business as a security-centric enterprise. Barracuda MSP enables IT managed service providers to easily scale their business with a combination of multi-layered security and data protection solutions, award-winning support, and MSP-friendly prices. Barracuda MSP's industry-leading IT security solutions are trusted by nearly 5.000 IT service providers worldwide.