
Aqua Security, the leader in cloud-native security, announces the results of the latest Software Supply Chain Security Review study into software supply chain attacks. Over a period of six months, the experts were able to determine that the attacks in 2021 tripled compared to 2020.
Cyber criminals target vulnerabilities in the software supply chain to inject malware and backdoors. To do this, they mainly use security gaps in open source software, inject malicious code (“poisoning”) and exploit general problems with the integrity of software code. The Software Supply Chain Security Review study was conducted by Argon Security, which was acquired by Aqua Security in December.
Software Supply Chain Security Review
In general, the experts found that the level of security in software development environments remains low and that each company examined has vulnerabilities and misconfigurations that can make it vulnerable to supply chain attacks. The study identified three main areas where risks may arise.
1. Use of vulnerable packages
Open source code is part of almost all commercial software. Many of the open source packages used have existing security vulnerabilities and updating to a more secure version requires a lot of effort for the development and DevOps teams. Unsurprisingly, this is one of the fastest growing methods of conducting attacks. There are two common attacks that exploit vulnerable packages:
- Existing vulnerability exploits: Existing package vulnerabilities are exploited to gain access to the application and execute the attack. (Example: recent Log4j cyber attacks)
- Package poisoning: Injecting malicious code into popular open source and proprietary software packages to trick developers or automated pipeline tools into including them in the application build process. (Example: The case of COA, RC and ua-parser-js)
2. Compromised pipeline tools
Attackers can exploit privileged access, misconfigurations, and vulnerabilities in the CI/CD pipeline infrastructure (e.g., source control system, build agent, package registrations, and service dependencies) that compromise critical IT infrastructure, development processes, source code, and applications Offer. A compromised CI/CD pipeline can expose an application's source code, which is the blueprint of the application, development infrastructure, and processes. This allows attackers to modify the code or inject malicious code during the build process and manipulate the application (as was the case with the SolarWinds attack, for example). This type of security breach is difficult to detect and can cause major damage before it is discovered and fixed.
Attackers also use compromised package registries to upload compromised artifacts instead of legitimate ones. In addition, there are dozens of external dependencies connected to the pipeline that can be used to access and attack (example: codecov).
3. Code/Artifact Integrity
One of the main risk areas identified in the study is the uploading of buggy code to source code repositories, which directly impacts artifact quality and security posture. Common issues found in most customer environments were sensitive data in the code, code quality and security issues in general, the infrastructure-as-code issue, vulnerabilities in container images, and general misconfigurations. In many cases, the number of problems discovered was so large that they could only be corrected with extensive projects.
Protection of the software supply chain
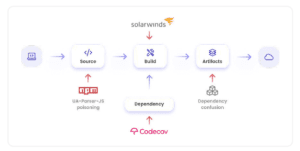
The attack points of the software supply chain with examples of known attacks (Image: Aqua Security).
To combat the problem and increase the security of the software supply chain, security teams need to increase collaboration with DevOps teams and implement security automation within development processes. Aqua and Argon recommend the adoption of new security solutions that can protect the software development process from this new wave of sophisticated attacks.
"The number of attacks over the past year and the far-reaching impact of a single attack underscores the serious challenges facing application security teams," said Eran Orzel, senior director of customer success and sales at Argon Security. “Unfortunately, most teams lack the resources, budget, and knowledge to deal with software supply chain attacks. Add to this the fact that AppSec teams rely on collaboration with development and DevOps teams to combat this attack vector and you can see why this is a big challenge. The software supply chain process is a core component in the modern application development lifecycle. Leaving this broad attack vector open threatens enterprise application security, potentially exposing sensitive data and creating additional entry points into the application at runtime. In many cases, security teams don't have visibility into this process until it's too late. Because most companies don't have preventative capabilities within their CI/CD tools and processes.”
More at Aquasec.com
About Aqua Security
Aqua Security is the largest provider of pure cloud-native security. Aqua gives its customers the freedom to innovate and accelerate their digital transformation. The Aqua platform provides prevention, detection, and response automation across the application lifecycle to secure the supply chain, cloud infrastructure, and ongoing workloads—regardless of where they are deployed. Customers include the world's largest companies in financial services, software, media, manufacturing and retail, with deployments across a wide range of cloud providers and modern technology stacks that include containers, serverless functions and cloud VMs.
