Trend Micro warns of ransomware targeting industrial control systems. Germany is particularly badly affected by grayware, and is in the global midfield for malware. The study “2020 Report on Threats Affecting ICS Endpoints” serves as the basis.
Trend Micro, a global leader in cybersecurity solutions, today released a new report highlighting the increasing risk of downtime and theft of sensitive data from ransomware attacks on industrial facilities.
Industrial control systems difficult to secure
“Industrial control systems are incredibly difficult to secure. This leads to numerous security gaps that cyber criminals are exploiting more and more precisely, ”says Udo Schneider, IoT Security Evangelist Europe at Trend Micro. "Given that the US government is now treating ransomware attacks with the same severity as terrorism, we hope that our latest study results will help industrial plant operators prioritize and realign their security efforts."
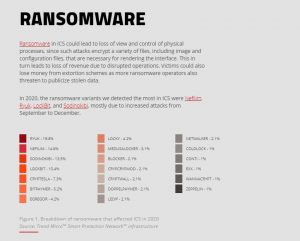
Industrial control systems (ICS) are used as an essential component of energy supply and manufacturing systems as well as other industrial operations to monitor and control industrial processes across IT-OT networks. If ransomware finds its way into these systems, it can paralyze operations for days and increase the risk of drafts, programs, and other sensitive documents finding their way onto the dark web. Trend Micro's report shows that variants of the Ryuk (20 percent), Nefilim (14,6 percent), Sodinokibi (13,5 percent) and LockBit (10,4 percent) malware families account for more than half of ICS Ransomware infections are responsible in 2020.
Well-known families of malware attack ICS
Compared to countries like Japan (4,7 percent) or the USA (9,8 percent), which, along with Germany, are among the ten countries with the largest number of IT / OT networks with ICS endpoints, Germany has 17,3, XNUMX percent has a comparatively high percentage of grayware. Grayware is a term used to describe potentially unwanted applications, adware (programs that display unwanted advertisements), or hacking tools. In addition, the study by the Japanese security provider found that industrial control systems in Germany are infected with the most adware worldwide - mostly due to programs that are bundled with software tools.
The study contains further findings
- Threat actors infect ICS endpoints to mine cryptocurrency using unpatched operating systems that are still vulnerable to EternalBlue.
- Variants of Conficker spread to ICS endpoints with newer operating systems by brute-forcing admin shares.
- Legacy malware like Autorun, Gamarue and Palevo are still everywhere in IT / OT networks and spread via removable drives.
The study calls on IT security and OT teams to work more closely together to identify important systems and dependencies, such as operating system compatibility and runtime requirements, in order to develop more effective security strategies.
Trend Micro makes the following recommendations
- Immediate patching of vulnerabilities is essential. If this is not possible, organizations should consider network segmentation or virtual patching.
- Organizations can combat ransomware after it penetrates by using application control software and threat detection and response tools to contain the root causes of the infection to search networks for Indicator of Compromise (IoC).
- Network shares should be restricted and strong username / password combinations should be enforced to prevent unauthorized access by brute-forcing credentials.
- IDS (intrusion detection systems) or IPS (intrusion prevention systems) can record normal network behavior and detect suspicious activities at an early stage.
- Companies should regularly scan ICS endpoints with standalone tools even in supposedly air-gap environments.
- USB malware scanners can be used to scan removable drives used to transfer data between air-gapped endpoints.
- Organizations should apply the principle of least privilege to OT network administrators and operators.
The full 2020 Report on Threats Affecting ICS Endpoints is available online in English.
More at TrendMicro.com
About Trend Micro As one of the world's leading providers of IT security, Trend Micro helps create a secure world for digital data exchange. With over 30 years of security expertise, global threat research, and constant innovation, Trend Micro offers protection for businesses, government agencies, and consumers. Thanks to our XGen™ security strategy, our solutions benefit from a cross-generational combination of defense techniques optimized for leading-edge environments. Networked threat information enables better and faster protection. Optimized for cloud workloads, endpoints, email, the IIoT and networks, our connected solutions provide centralized visibility across the entire enterprise for faster threat detection and response.