
Proofpoint has discovered potentially dangerous Microsoft Office 365 features that attackers use to delete recovery version files stored on SharePoint and OneDrive in order to more easily blackmail victims.
Ransomware attacks traditionally target data across endpoints or network drives. Until now, IT and security teams have believed that cloud drives are more resilient to ransomware attacks. After all, the now well-known “AutoSave” feature, along with versioning and the good old recycle bin for files as a backup, should have sufficed. But that might not be the case for much longer.
Vulnerability in Microsoft 365 and OneDrive
Proofpoint has discovered a potentially dangerous feature in Office 365 or Microsoft 365 that allows ransomware to encrypt files stored on SharePoint and OneDrive in a way that makes them unrecoverable without dedicated backups or a decryption key from the attacker. The research focused on two of the most popular cloud apps for business - SharePoint Online and OneDrive within the Microsoft 365 and Office 365 suites - and shows that ransomware actors are now targeting corporate data in the cloud and launching attacks on cloud infrastructure be able.
Cloud ransomware attack chain
The Attack Chain: Proofpoint has identified the attack chain and documented the following steps. Once executed, the attack encrypts the files in the compromised users' accounts. As with endpoint ransomware activities, these files can only be accessed using decryption keys.
The actions described below can be automated using Microsoft APIs, Command Line Interface (CLI) scripts, and PowerShell scripts.
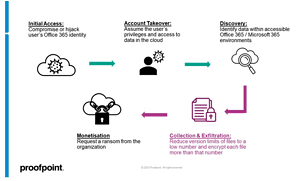
Cloud ransomware attack chain diagram. The capture and exfiltration phase is unique in Microsoft environments (Image: proofpoint).
- Initial access: Attackers gain access to one or more users' SharePoint Online or OneDrive accounts by compromising or hijacking the users' identities.
- Account takeover and discovery: The attacker now has access to all files owned by the compromised user or controlled by the third-party OAuth application (which would also include the user's OneDrive account).
- collection and exfiltration: Now the versioning limit of files is reduced to a low number, e.g. B. 1 to keep it simple. Then the file will be encrypted more times than the version limit. With the example limit of 1, the file will be encrypted twice. This step is unique to cloud ransomware compared to the attack chain for endpoint-based ransomware. In some cases, the attacker can exfiltrate the unencrypted files as part of a dual blackmail tactic.
- Monetization: Now all original versions (before the attacker) of the files are lost, leaving only the encrypted versions of each file in the cloud account. At this point, the attacker can demand a ransom from the organization.
Microsoft declines
Microsoft informed Proofpoint that older versions of files can still be recovered within 14 days of an attack with the help of Microsoft Support. However, Proofpoint tested this and determined that restoring encrypted files this way does not work. In a blog post, proofpoint looks at the attack and settings in OneDrive as well as in SharePoint in even more technical detail.
More at proofpoint.com
About Proofpoint Proofpoint, Inc. is a leading cybersecurity company. The focus for Proofpoint is the protection of employees. Because these mean the greatest capital for a company, but also the greatest risk. With an integrated suite of cloud-based cybersecurity solutions, Proofpoint helps organizations around the world stop targeted threats, protect their data, and educate enterprise IT users about the risks of cyberattacks.
