The new DDoS report from Link11 in the middle of the year shows: In addition to the increase in the number of attacks by a third compared to the same period in the previous year, the number of high-volume attacks has also increased.
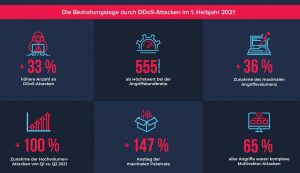
Link11, the leading European IT security provider in the field of cyber resilience, published the annual Link11 DDoS report in the middle of the year. The report shows that DDoS criminals were again very active in the first half of the year. They launched a record number of attacks. The Link11 Security Operations Center (LSOC) recorded a third (33%) more attacks than in the same period of the previous year in the DDoS record year 2020. The attacks were already at a high level in 2020 and have increased significantly compared to the previous year. This trend continues suddenly. Within the first half of the year, the number and severity of DDoS attacks increased noticeably again. The LSOC registered 2% more attacks in the 19nd quarter than in the previous quarter. Nevertheless, this was already characterized by a large number of attacks, including on vaccination centers and home schooling platforms.
High attack volumes combined with long duration
The report also shows that numerous attacks had an attack volume of over 100 Gbps. Their number has increased compared to the previous year: from 30 to 40 attacks. In addition, there were hundreds of attacks with bandwidth peaks between 20 and 100 Gbps. Whether by means of hijacked cloud accounts or botnets - these attack bandwidths are becoming more and more normal. In addition, many of these high-volume attacks dragged on for hours. High-bandwidth attacks usually end after a few minutes in order to protect the attacker's resources. The largest attack of the first half of the year stopped at 555 Gbps and exceeded the maximum attack bandwidth of the same period of the previous year by almost 38%.
The most important countries of origin for attacks were the USA and Germany
The devices and servers that attackers misused for DDoS attacks were distributed around the world. In the first half of the year, most of the inquiries about DDoS attacks came from the USA. The second most frequent attacks could be traced back to Germany. DDoS traffic from Russia and China, which has made up a large part of the data traffic in recent years, has decreased significantly.
Ransomware DDoS extortion on the rise
Particularly noteworthy is the increasing number of DDoS extortions. Since the beginning of 2021, several of these waves (RDDoS - Ransom Distributed Denial of Service) have been directed against companies from the finance, e-commerce, media and logistics, industry, consumer goods, telecommunications and hosting provider / ISP sectors. Blackmail activities peaked in January and June, which required a variety of emergency integrations. The acts recently presented themselves as the "Fancy Lazarus Group". The procedure of the perpetrator or perpetrators was largely identical to the criminal activities of the DDoS extortionists who had been operating under the names Armada Collective, Fancy Bear and Lazarus-Group since summer 2020.
An end to the current wave of ransom demands in the current third quarter is not in sight, warns the LSOC. Rather, companies have to adapt to the fact that cyber extortion with DDoS attacks is becoming an integral part of the threat landscape and is increasingly being combined with other attack techniques - especially ransomware.
DDoS attacks become part of the threat landscape
Marc Wilczek, Managing Director of Link11: “In the first half of the year we registered an unbelievably large number of DDoS attacks and extortions. For companies that were inadequately protected, this was often a major challenge, as we noticed from the high number of emergency missions. Existing tools and systems also regularly reached their limits, something that some companies only realized in an emergency. If the acute threat is over, such an incident offers security officers the opportunity to rethink their own strategies and to close the gaps in their own IT security defense systems. Because prevention is better than emergency management. "
More at Link11.com
Via Link11 Link11 is the leading European IT security provider in the field of cyber resilience, with headquarters in Germany and worldwide locations in Europe, North America, Asia and the Middle East. The cloud-based security services are fully automated, react in real time and repel all attacks, both known and new patterns, guaranteed in less than 10 seconds. According to the unanimous opinion of analysts (Gartner, Forrester), Link11 thus offers the fastest detection and defense (TTM) available on the market. The Federal Office for Information Security (BSI) identifies Link11 as a qualified DDoS protection provider for critical infrastructures. To ensure cyber resilience, web and infrastructure DDoS protection, bot management, zero-touch WAF and even secure CDN services ensure holistic and cross-platform hardening of networks and critical applications in companies.