
Iranian-led APT group Charming Kitten (aka Mint Sandstorm) is behind the new BellaCiao malware campaign targeting organizations in the US, Europe, Israel, Turkey and India. New to the attack: The malware is used as hard code.
In its current report, Bitdefender Labs analyzes the attack methods of the new active malware campaign BellaCiao. The well-known Iranian Charming Kitten group uses it to initially search for vulnerabilities in an opportunistic and automated manner before launching highly sophisticated malware attacks that are individually tailored to the individual victims. They then attack the targets using a novel command-and-control (CC) infrastructure. Hackers can exploit the backdoor and dropper capabilities to hard-code any espionage, data-stealing, or ransomware malware instead of downloading it. The first developers of the malware dubbed their attack campaign BellaCiao.
Charming Kitten supported by the Iranian state
Charming Kitten (also known by the names APT35/APT42, Mint Sandstorm/PHOSPHORUS, ITG18, UNC788, Yellow Garuda, or TA453) is an Iranian state-backed APT group affiliated with the Guardians of the Islamic Revolution (Revolutionary Guard) Army . Charming Kitten has been known among IT security experts since 2014 for targeting the political opposition, activists, journalists and individual anti-regime actors. The group mostly relied on social engineering or spear phishing for this, but also used sophisticated attack methods such as impersonating well-known researchers or activists. Since 2021, the Revolutionary Guards and associated APT groups have become increasingly aggressive.
New step: Malware as hard code
With BellaCiao, the members of the Charming Kitten group use a new way of playing out their commands from the CC server to the existing endpoint. To do this, BellaCiao asks the affected systems to start a DNS request on their behalf every 24 hours. The DNS server controlled by the hackers then sends a resolved IP address that almost matches the actual public IP address. The command and control server sends its commands via a hard-coded string instead of traditional downloads. The further action of the malware is disguised as a legitimate IT process.
The string is set individually for each attacked company according to the pattern:
<2 random uppercase letters><3 random lowercase letters> .
All samples observed by Bitdefender include .pdb paths. PDB (Program DataBase) is a file format for Microsoft Visual Studio and stores debugging informaion about an executable or a DLL file. The paths then contain the information for the attacks on each individual customer, sorted by country.
Hybrid attacks: From automated opportunism to targeted manual attacks. With BellaCiao, the hackers use a targeted malware attack that is based on opportunistic attacks.
Always looking for remote vulnerability
Commercially motivated or state-supported APT hackers like Charming Kitten are currently increasingly looking for Remote Code Execution (RCE) vulnerabilities – preferably those for which a PoC is already publicly known. Building on this, they want to attack as many companies as possible using opportunistic methods. They discover vulnerable systems with automated scans and compromise them with a malicious payload using a spray-and-pray tactic. This is usually worthwhile: Even if software manufacturers publish a patch against the vulnerability, on average tens of thousands of systems worldwide remain unpatched and therefore vulnerable. Next, the attackers then implement a webshell.
The persistent intrusion into the victim network is followed by targeted attacks, in this case with BellaCiao. Weeks or months can sometimes elapse between the opportunistic start and the actual execution of an attack. Companies from every industry and of different sizes are affected.
Microsoft Defender can then be deactivated
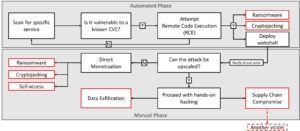
🔎 Hybrid attacks: Economically oriented and state-supported hackers first search automatically and opportunistically for as many victims as possible, who they then attack manually and specifically (Image: Bitdefender).
Attackers can then perform numerous actions, such as deactivating Microsoft Defender or stealing password information. A variant of BellaCiao implements the Plink command line tool for a reverse proxy connection to the command and control server. As a result, hackers can use Powershell to run commands and scripts, upload or download files, or shut down a web server. The Bitdefender experts also expect attacks on Microsoft Exchange servers.
Consistent patching of known vulnerabilities is particularly recommended as a defense against such hybrid attacks. If such are known, every company should assume that the hackers will also follow up on such a tip. Equally important is the reduction of the attack surface, proactive detection and defense as well as threat intelligence based on IP, domain and URL reputation. The security experts in a security operation center identify individually modified attacks.
More at Bitdefender.com
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de
