Today, data security and the security of the digital infrastructure are crucial for the success of a company. Companies are generating new data at astronomical speeds. Data has long since become a digital currency - and its value is increasing every day. Immutable Storage ensures more data security.
Thus, protection against security threats and other data loss is of paramount importance for the IT security and administration teams. Data consistency and authenticity must be assured as organizations grapple with industry and government compliance mandates and other SLAs. But data protection against external attackers and malware also plays a major role.
Often, however, the protection of this data is only viewed very one-sidedly and the entire backup path is only viewed as a worst-case scenario.
Backups are a good place to start
It is now a common practice to back up data to the last known clean state in the event of data corruption or loss. But what happens when that backup itself falls victim to a security breach? According to a recent Veeam study, over 90% of all attacks target backups first. Almost three quarters are even successful.
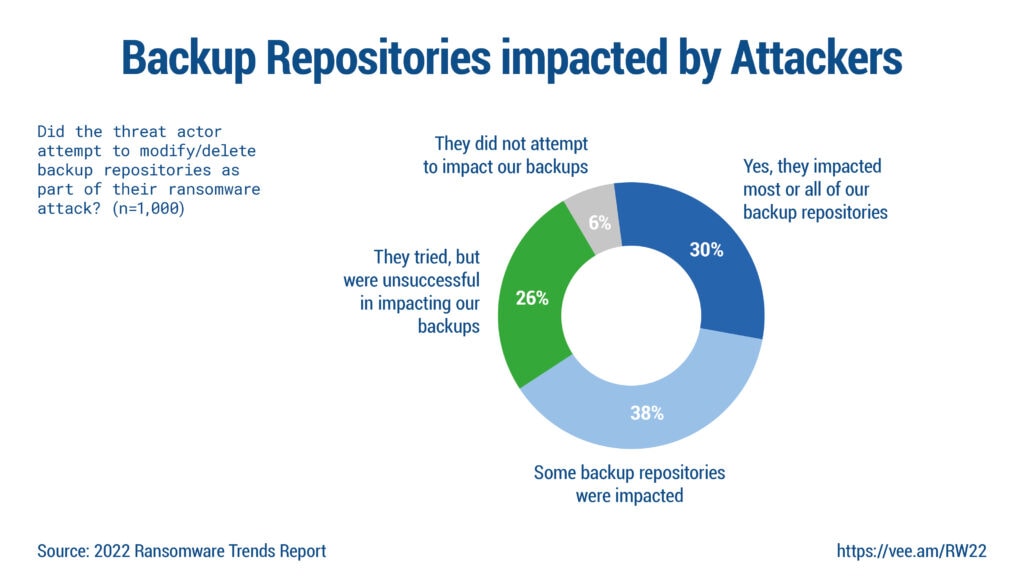
🔎 Cyber thugs are increasingly targeting company backups to prevent them from recovering from ransomware attacks; Immutable Storage protects the backups (Image: FAST-LTA).
It is important to set up effective security mechanisms to protect stored data (primary data and backups) from unwanted and unforeseen data protection breaches - whether from the inside or from the outside. And in order not to have to pay high ransom demands and hope for the decryption of the data.
Data must not be changeable
The answer to this data security challenge is: Immutable storage, i.e. immutable storage.
The principle of immutable storage is that data cannot be tampered with or deleted by anyone, regardless of their intent. Once immutability is set for a period of time, the data will remain in its original and unaltered form until that period of time has expired. During this time, the data is immutable and non-erasable, so both data retention and data integrity requirements are met.
Key Applications and Benefits of Immutable Storage
- Protection from ransomware and other cyber-attacks: Immutability ensures primary data and backups cannot be encrypted or altered, making them impervious to malicious actors
- Prevention of malicious insider threats, e.g. B. when a disgruntled employee tries to delete or modify secure files
- Preventing users from accidentally deleting files and modifying content
- Protection against human errors and bugs that lead to data corruption
- Complying with policies that dictate that exact copies of data must be retained for a specified period of time (video and audio surveillance footage, backups, log files, historical analytics data, etc.)
- Maintaining data authenticity for litigation needs, such as B. Legal retention periods, providing a chain of evidence and securing digital evidence
- Protection of backups from retention policy changes and deletion of recovery points
How should you react?
A concept of immutability of data can be implemented on different storage media and using different technologies. You can find out what these are and how you can meet your requirements in our exclusive white paper "Immutable Storage".
To the white paper at FAST-LTA.de
About FAST LTA the FAST LTA is the specialist for secure secondary and long-term storage systems. The combination of durable and low-maintenance hardware, integrated software for data backup and on-site maintenance contracts with a term of up to 10 years ensure long-term, cost-effective storage of data from archive and backup applications. In-house developments such as local erasure coding, sealing using hardware WORM and efficient energy management help medium-sized customers to protect themselves against data loss through ransomware attacks and misconfiguration and to meet regulatory and legal requirements (GDPR). The Munich provider's solutions have proven themselves in thousands of installations in healthcare, public administration, film/TV/video and industry.
