
Attackers use SSRF vulnerability for extremely large-scale Exchange server takeovers. However: Exchange hackers capitulate to Office 365. A comment from Dr. Klaus Gheri, General Manager Network Security at Barracuda Networks.
An outcry has raged through the Exchange email server community since last week after Microsoft announced that a cybercrime group known as Hafnium was launching its attack campaign to target vulnerabilities around Microsoft Exchange's Outlook Web Access interface exploits. And there are many weak points. The headlines that have been produced since then are correspondingly drastic. In general, companies across Germany are affected, in particular several federal authorities, including the Federal Environment Agency, which then sent its entire e-mail system to quarantine, or the Paul Ehrlich Institute. In principle, IT security in Germany is disastrous.
But this campaign is not that new. The latest studies have shown that the attacks have been going on for over two months. Nonetheless, they have had a massive impact and have hit around 60.000 targets worldwide so far. But what exactly is behind it? More importantly, what can organizations do about it?
Exchange takeover in vulnerable systems
The vulnerabilities that were exploited were CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065. CVE-2021-26855 is a server-side request forgery (SSRF) vulnerability in Exchange that allows attackers to send arbitrary HTTP requests and authenticate themselves as an Exchange server. CVE-2021-26855 is the preferred choice to identify vulnerable systems. The remaining vulnerabilities appear to be chained to this vulnerability in order to carry out further exploits, including so-called webshells. A webshell is a malicious web-based interface that allows remote access and control of a web server by executing any command.
Attacked URLs
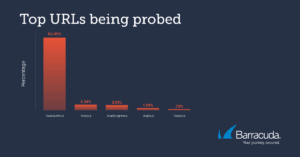
Before the Exchange attack, the attackers probed a few URLs particularly frequently (Image: Barracuda).
The security analysts at Barracuda have noticed an initially moderate and later significant increase in probing attempts for CVE-2021-26855 since the beginning of March. A considerable number of these were directed against systems that did not run Exchange in the backend. The most common URLs the attackers probed were:
- /owa/auth/x.js
- /ecp/y.js
- /ecp/program.js
- /ecp/x.js
- //ecp/x.js
Apparently most of these probes used the X-AnonResource-Backend and X-BEResource cookies. Both ended with the parameter “?~3”. The Microsoft script describes this for scanning security risks. The UserAgents used by these scanners were mainly ExchangeServicesClient, python-requests and nmap. In addition, standard browser headers were also used. It can be assumed that the attackers will continue to look for the vulnerabilities mentioned and exploit them for a few more weeks before the attacks level off at a lower level.
Unsuccessful attacks on Office 365 email environments
An important finding from the security analyzes is that the hackers with their attacks against companies that use Office 365 ran into locked security doors and were unsuccessful. Obviously, as many security experts have repeatedly emphasized, the cloud is more secure than outdated, local solutions. Hafnium has shown that the cloud is not yet an option for many organizations and companies. Why is that?
Missing information
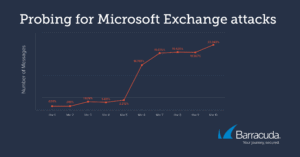
Since the beginning of March there has been an initially moderate and later significant increase in probing attempts for CVE-2021-26855 (Image: Barracuda).
Either the advantages of a migration to the cloud are not fully understood or you are afraid to take the first step towards migration. So for the time being everything stays the same, i.e. with the existing local approach.
Fear of losing control
Often there is a feeling of having less control over resources and workloads in the cloud than with local servers, even though they take more time to manage and are not as secure.
Existing regulations
In certain highly regulated industries, organizations must comply with a variety of data storage and retention requirements, which can make moving to the cloud difficult.
Using a cloud-hosted email provider allows system updates and security patches to be deployed more quickly to protect against zero-day attacks like the latest from Hafnium. Since Microsoft is one of the most frequently attacked platforms for cyberattacks, it is generally advisable to supplement Microsoft's existing security with a third-party provider.
OWA without firewall protection is daring
In general, placing Outlook Web Access (OWA) on the Internet without further protection by a firewall has always been a daring approach. However, the incident can serve as a wake-up call that the independent operation of such infrastructure services is an anachronism in times of the public cloud. The modern counterpart is Microsoft 365 with Azure Active Directory. The service is maintained and secured by Microsoft so that weaknesses can be rectified immediately. It is now high time for everyone concerned to think about a change and to master the patch management and additional protection of Outlook Web App until then. Unfortunately, the way is not so easy for everyone, as in some areas regulations restrict the use of services in the public cloud. One should think seriously about this in view of the massive data loss that has occurred here in many organizations.
More at Barracuda.com
Via Barracuda Networks Striving to make the world a safer place, Barracuda believes that every business should have access to cloud-enabled, enterprise-wide security solutions that are easy to purchase, implement and use. Barracuda protects email, networks, data and applications with innovative solutions that grow and adapt as the customer journey progresses. More than 150.000 companies worldwide trust Barracuda to help them focus on growing their business. For more information, visit www.barracuda.com.
