A new, free self-hacking tool allows companies to safely hack their own network and check their DNS security. EfficientIP introduces the tool for detecting the risk of data exfiltration in companies.
The free self-hacking tool, a DNS-based data exfiltration application, is free for companies to use. Designed as an easy-to-use online tool, the application enables organizations to easily and securely conduct their own 'ethical hack' of their DNS systems and associated security measures. In this way, vulnerabilities can be uncovered that could lead to a larger security gap in the network and thus also to a data leak.
Self-Hack finds the vulnerabilities
As the foundation of all networks and IP-based services and businesses, the DNS (Domain Name System) is a popular target for cybercriminals to break into a network, exploit vulnerabilities and exfiltrate critical data for malicious purposes. A study conducted in partnership with research firm IDC found that 88% of organizations surveyed experienced at least one DNS attack on their business over a 12-month period, with nearly a quarter (24%) of organizations reporting the theft of sensitive customer information or intellectual property about the DNS was affected.
DNS-based Data Exfiltration Application
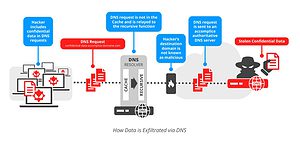
EfficientIP's DNS-based Data Exfiltration Application helps organizations protect themselves more effectively from attacks and stay one step ahead of attackers by allowing them to test their own DNS networks. This helps determine if they are vulnerable to the techniques attackers use to breach network security. With data exfiltration, using techniques similar to DNS tunneling, attackers follow what is known as a “low-and-slow” approach, where attackers are careful to avoid a large spike in DNS traffic and thus no attention to arouse. In doing so, they extract smaller packets of data via legitimate DNS queries to the server and reconstruct the information once this process is complete.
“Data exfiltration via DNS is one of the most complex and difficult to identify attack vectors, but it can cause significant damage to organizations. It's difficult to detect even for the trained human eye, and with many traditional security solutions failing to detect exfiltration in legitimate traffic and DNS requests, organizations can be hit by a data breach long before they know it." , said Norman Girard, CEO of EfficientIP.
Data exfiltration via DNS is difficult to identify
He continues: “Together with our partner network, we want to enable organizations to test their systems and identify vulnerabilities so that they can prevent data theft in the first place. Security breaches and data theft can be costly to any business, whether through fines, loss of intellectual property, or loss of customer trust. Your DNS doesn't have to be your security hole. Effective DNS monitoring is an important requirement for protecting sensitive data.”
The new DNS-based data exfiltration application, powered by EfficientIP and its network of channel partners, enables organizations to quickly identify gaps and potential vulnerabilities in their network and implement appropriate countermeasures to mitigate the risk of an attack in the future. With effective DNS security checks, organizations protect against data exfiltration while meeting compliance regulations.
More at efficientIP.com
About EfficientIP
EfficientIP is a computer network automation and security company specializing in DNS-DHCP-IPAM (DDI) solutions. Our goal is to help organizations across all industries increase their operational efficiencies through an agile, secure and reliable infrastructure foundation.