Proofpoint security experts have uncovered a new hacker group called TA866, which attacked tens of thousands of companies with malware between October 2022 and January 2023. The activities are aimed in particular at organizations in Germany and the USA.
One detail of the TA866 attacks stands out: the cybercriminals first analyze screenshots of their potential victims' IT environments to identify particularly lucrative targets. They only try to infect the victim with a bot or a stealer if they think it is worth further involvement.
Attack launch with screentime
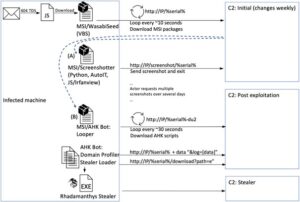
From October 2022 through January 2023, Proofpoint observed a cluster of financially motivated activity that experts refer to as "screentime." The chain of attacks starts with an email that contains a malicious attachment or URL. Both lead to malware known as "WasabiSeed" and "Screenshotter". In some cases, Proofpoint observed activities that included AHK Bot and Rhadamanthys Stealer following the primary infection.
Most campaigns in October and November 2022 consisted of a limited number of emails and focused on a small number of companies. The campaigns were observed on average once or twice a week and the messages contained attached publisher files. In November and December 2022, around the time the group transitioned to using URLs, the scale of operations increased and email volume increased dramatically. Typical campaigns comprised thousands or even tens of thousands of emails and could be observed two to four times a week. In January 2023, the frequency of campaigns decreased, but email volume grew even more.
The chain of infection
On January 23 and 24, 2023, Proofpoint observed tens of thousands of email messages targeting over a thousand companies. The messages targeted organizations in the US and Germany. The e-mails sent seemed to rely on thread hijacking and lured with subject lines such as "Check my presentation". These messages contained malicious URLs that launched a multi-stage chain of attacks. When a user clicks on the URL, they set the chain of attacks in motion. In a blog post at Proofpoint, all the individual steps are examined and documented using various screenshots.
More at proofpoint.com
About Proofpoint Proofpoint, Inc. is a leading cybersecurity company. The focus for Proofpoint is the protection of employees. Because these mean the greatest capital for a company, but also the greatest risk. With an integrated suite of cloud-based cybersecurity solutions, Proofpoint helps organizations around the world stop targeted threats, protect their data, and educate enterprise IT users about the risks of cyberattacks.