
According to a new study by Bitdefender Labs, all MS Office applications (including Outlook, Word, Excel, OneNote and PowerPoint) are vulnerable to international domain name (IDN) homograph phishing attacks in order to redirect users to different addresses.
Bitdefender has consistently observed such homograph phishing for several months and strongly advises companies to take countermeasures to avoid associated risks. Bitdefender Labs reported this issue to Microsoft in October 2021 and the Microsoft Security Response Center has confirmed the results as valid. It is still unclear if or when Microsoft will fix this problem.
IDN domain is spoofed for attack
In practice, these attack possibilities mean the following: An IDN domain also consists of characters that do not belong to the standard ASCII character set and contain umlauts or special characters. This domain can become the perfect mask for the original legitimate domain that the user thinks they are visiting. Regularly occurring homograph phishing attacks are based on the fact that outwardly identical characters, such as the Cyrillic "a" and the Latin "a", are different characters according to the Unicode standard. The Unicode standard specifies how a character is stored electronically. The Latin "a" has the code "U+0061", the Cyrillic "a" the code "U+0430". The IDN "apple.com" cannot therefore contain a Cyrillic "a" or a Cyrillic "e". Anyone who clicks on them does not end up with the hardware manufacturer, but rather on a website operated and used by hackers.
For example, in the Word preview, the homograph IDNs supposedly pointing to legitimate websites are shown, which in fact point to a fake website. Legitimate website and fake IDN are indistinguishable and remain masked in Office even when previewed, greatly increasing the likelihood of clicking a malicious link.
Wrong domains in Microsoft Office remain masked
The idea is not new. However, it now affects the entire Microsoft Office package. Although the risk of IDN homograph attacks in web browsers has been raised, Bitdefender has found that malicious IDNs remain masked in the MS Office applications, increasing the likelihood that even a security-conscious user will click on the wrong domain. (Figures 1-3). The view in the browser then unmasks the malicious site - but only in most cases. In addition, hectic or fast-acting users may not notice the unmasking in the browser or may notice it too late, make the mistake and actually open the previously camouflaged website.
Bitdefender tested applications other than Microsoft Office with mixed results: some always visibly displayed the actual, i.e. malicious, address the user landed on, while others displayed the homograph.
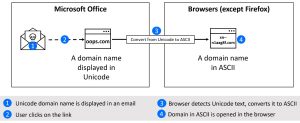
Microsoft Office displays the IDN normally in Unicode - but unescaped in ASCII it is malicious. (Image: Bitdefender).
Targeting financial institutions and crypto exchanges
Attacks based on homograph IDNs are not easy to carry out. However, they are an effective tool for cybercriminals who want to launch complex attacks with their Advanced Persistent Threats (APT) and for ransomware as a service. Bitdefender observed spoofing against financial institutions and cryptocurrency exchanges.
Bitdefender security recommendations
Companies and users can protect themselves against attacks with homograph IDNs with the following measures:
- Awareness raising: Companies should draw particular attention to the danger to those employees who, because of their position, are a possible victim of spear phishing attacks. A check of the URL and the lock icon is not sufficient in this case.
- Endpoint Protection: Endpoint Detection and Response detects and blocks malicious websites.
- Reputation check: IP and URL reputation services should be running on all devices. A rule of thumb: if the URL starts with xn--, the website is suspicious.
- Multi-factor identification on company-owned pages means that such an attack is in vain and hackers can no longer access login information.
- Browser Updates: Web browsers and other productivity tools should always be up to date.
- Keep an eye on the supply chain: Homographs can get into the company's IT via the supply chain. Documents from suppliers, customers or partners must therefore be checked.
- Register domains broadly: Businesses should be aware of all domains in their various Unicode spellings that could be associated with your business. Then hackers can not monopolize these pages for themselves. Since IDNs are limited to a single Unicode character set, the possible combinations and thus the number of websites to be registered are limited. Bitdefender Labs found that few companies proactively register all potential spoofing domains.
About Bitdefender Bitdefender is a leading global provider of cybersecurity solutions and antivirus software, protecting over 500 million systems in more than 150 countries. Since it was founded in 2001, the company's innovations have consistently ensured excellent security products and intelligent protection for devices, networks and cloud services for private customers and companies. As the supplier of choice, Bitdefender technology is found in 38 percent of security solutions deployed around the world and is trusted and recognized by industry experts, manufacturers and customers alike. www.bitdefender.de
