
The DarkSide ransomware attack on the colonial pipeline in the USA is just one of many examples that have spread around the world that security is not just a matter of IT, but also of strategic planning and management. 5 insights from Sophos experts.
The DarkSide ransomware attack on the colonial fuel pipeline, which supplies about 45 percent of the diesel, gasoline and aircraft fuel on the US East Coast, is just one example that now joins over 60 known cases. Ireland's health service, Toshiba Europe and the Essen chemical company Brenntag are also among the alleged victims. Time and again, incident forensics point out problems within the IT network that existed before the incident and that contributed to the vulnerability to attacks. Consequently, the question arises as to why those affected did not exhaust all potentially possible security precautions and whether there was a dedicated person responsible for cybersecurity in the organization at the time of the ransomware attack. John Shier, Senior Security Advisor at Sophos, summarizes the five most important findings from the attacks since May 2021.
IT security priority
In today's dangerous situation, companies and organizations need a person in charge who has an eye on the current risk situation, who is familiar with security and who sits on the company's management committee: the Chief Information Security Officer (CISO). Even if a dedicated CISO is difficult to justify for some companies, there should be an adequate person who knows how to correctly set the priorities for IT security and who also enforces them. For example, at the Colonial hearing before the Senate, it became known that around 200 million US dollars had been invested in IT over the past five years - without any precise information on how much of it actually went into IT security.
The ability to prioritize corporate cybersecurity, have a sufficient budget, and have the necessary powers to enforce the priorities are essential for cybersecurity.
Security standards used
In many cases that the Sophos Rapid Response team has investigated, the initial point of entry into the network is a single stolen password, mostly for remote services. In Colonial's case, the attackers used the stolen password to gain access to a VPN service that did not have multi-factor authentication (MFA) enabled. The pipeline operator believed that this VPN profile was not in use and probably paid less attention to it - a typical situation that the experts observe again and again. There is a good chance that the attackers obtained the password through an earlier break-in in order to use it for their ransomware attack some time later. This leads to two extremely important consequences: Available security technologies such as MFA should always be activated and the security specialists should take minor and past security incidents seriously, as they can be the harbingers of major attacks.
Visibility of network events
Often times, the Sophos Rapid Response team finds that victims do not notice a ransomware attack until the ransomware has actually started and the data is encrypted. However, the attackers are usually online long before the ransomware is activated. Preparations by the attackers can take days or even months in order to cause the greatest possible damage or extort profit. In its Active Adversary Playbook 2021, Sophos assumes an average time the attackers stay in the victim's network of eleven days. Colonial was also one of the companies that did not have the transparency and visibility required to identify the attackers at an early stage. Therefore, Endpoint Detection and Response (EDR) tools are of great value not only to prevent attacks, but also to enable the business to scan for latent threats.
Emergency planning
Large companies or operators of important infrastructures in particular usually have good contingency plans for events in production, for defects, accidents and other traditionally classic events. However, cyber threats still seem to be seldom anchored in such plans - as is the case with Colonial. Emergency plans are vital. Organizations of all sizes should conduct a security assessment and plan how to respond to potential incidents. Some of the assessments can be carried out in-house, others with external specialists. Afterwards it is necessary to develop plans to a) better secure the weakest areas, b) have a process in case something goes wrong and c) test countermeasures based on the improvement and response plan.
Especially for companies and organizations in particularly important areas, information from sources such as the Information Sharing and Analysis Center (ISAC) should also be included. These organizations collect, analyze, and disseminate threat intelligence and provide tools to mitigate risk and improve resilience.
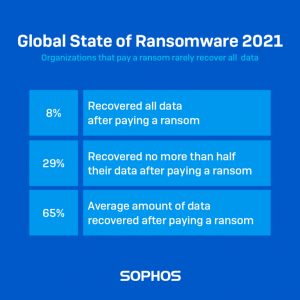
Pay or not pay
Time and again, companies are inclined to pay high ransom sums to the attacker out of an emergency. There are many examples where organizations have been forced to respond because their backups were corrupted or missing. Others want the network back up and running as quickly as possible, and still others choose to pay because it seems cheaper than the cost of restoring it. Another common reason is to prevent stolen data from being sold or made public. Colonial also gave one of these reasons as a justification for the payment.
Quintessential evaluation
The increasing criminal intensity, creativity and intelligence of the attackers will not be contained, the developments of the last few years describe the opposite. However, there are many and often not used options to reduce the potential risk.
“An attack shouldn't be necessary first for a company or organization to take a stronger position in the field of cybersecurity. You should now take the time and the resources to assess the security situation in order to then immediately and with the highest level of competence - both internally and with external specialists - establish a better and early defense wherever possible ", sums up John Shier .
More at Sophos.com
About Sophos More than 100 million users in 150 countries trust Sophos. We offer the best protection against complex IT threats and data loss. Our comprehensive security solutions are easy to deploy, use and manage. They offer the lowest total cost of ownership in the industry. Sophos offers award-winning encryption solutions, security solutions for endpoints, networks, mobile devices, email and the web. In addition, there is support from SophosLabs, our worldwide network of our own analysis centers. The Sophos headquarters are in Boston, USA and Oxford, UK.
